
XSS JUN 2021 - Cross-Site Scripting JUN 2021
Managed WordPress Security Report
Be informed about the latest Cross-Site Scripting JUN 2021, identified and reported publicly. As these XSS JUN 2021 vulnerabilities have a severe negative impact on any WordPress Security, consider our FREE security AUDIT.
An estimated jaw-dropping 3.396.200+ active WordPress installations were susceptible to these attack types, considering only the publicly disclosed and available numbers. The estimated number can increase by 20-25% with premium versions as they are private purchases.
Furthermore, the initial estimation can triple if we consider (1) the already patched versions BUT NOT UPDATED by owners, as the vulnerability remains active within their domain; and (2) the closed "uncounted" versions remain active on domains already running the plugins, as nobody is maintaining security. As these owners start changing their hosting provider (due to constant unexplained issues), they actively migrate these vulnerabilities behind new / protected areas, possibly exposing other clean WP to different attack types.
It is a whooping 290% increase compared to December 2020. We compare last month versus previous winter holiday season, which has the biggest shopping traffic and attack spike throughout the year. Read more about our previous reports here: ALERT: 27 XSS MAY 2021 – Cross-Site Scripting MAY 2021 Blast and 11 XSS – Cross-Site Scripting – WordPress Security DEC. The following cases made headlines PUBLICLY just last month in the XSS JUN 2021 category:
Hire security geeks to protect your WP from publicly reported cases of XSS JUN 2021 BEFORE IT’S TOO LATE! You will also protect your customers, your reputation and your online business!
- VikRentCar Car Rental Management System - CSRF to Stored XSS
- The popular car rental management system is now available also for WordPress as a Native Plugin! Active installations: 800+
- CityBook - Directory & Listing WordPress Theme - Unauthenticated Reflected Cross-Site Scripting (XSS)
- CityBook – Directory & Listing WordPress Theme is perfect if you like a clean and modern design. CityBook a listing directory theme that will help you create, manage and monetize a local or global directory site.
- iFlyChat - Authenticated Stored Cross-Site Scripting
- This plugin has been closed as of May 10, 2022 and is not available for download. Reason: Security Issue.
- Easy Preloader - Authenticated Stored Cross-Site Scripting
- This plugin has been closed as of May 4, 2022 and is not available for download. Reason: Security Issue.
- Cookie Law Bar - Authenticated Stored Cross-Site Scripting
- A simple and lightweight cookie law WordPress plugin for show information that your website uses cookie. Perfect for implementation of EU cookie law! Active installations: 5,000+
- Gallery From Files - Reflected Cross-Site Scripting
- This plugin has been closed as of May 24, 2022 and is not available for download. This closure is temporary, pending a full review.
- Visitors - Unauthenticated Stored Cross-Site Scripting
- This plugin has been closed as of May 26, 2022 and is not available for download. This closure is temporary, pending a full review.
- The Plus Addons for Elementor - Reflected Cross-Site Scripting
- Collection of 120+ Powerful Elementor Widgets, 18+ Templates, 300+ UI Blocks and Amazing Listing Builder for Post Types to surprise your clients with amazing Websites.
- Best Image Gallery & Responsive Photo Gallery – FooGallery - Authenticated Stored Cross-Site Scripting
- Make gallery management in WordPress great again! With FooGallery you can easily add a stunning photo gallery to your website in minutes. Active installations: 200,000+
- Event Calendar WD - Cross-Site Scripting
- Event Calendar WD is the most powerful plugin to create events and organize them into calendars. Active installations: 20,000+
- All 404 Redirect to Homepage - Authenticated Stored Cross-Site Scripting
- This plugin has been closed as of June 1, 2022 and is not available for download. This closure is temporary, pending a full review.
- WordPress Payments Plugin | GetPaid - Authenticated Stored Cross-Site Scripting
- GetPaid can be used as a payment system for 3rd party plugins too. Active installations: 4,000+
- Quiz And Survey Master – Best Quiz, Exam and Survey Plugin for WordPress - Unauthenticated Stored Cross-Site Scripting
- Quiz and Survey Master is the easiest WordPress Quiz Plugin which can be used to create engaging content to drive traffic and increase user engagement. Everything from viral quiz, trivia quiz, customer satisfaction surveys to employee surveys. This plugin is the ultimate marketing tool for your website. Active installations: 40,000+
- Quiz And Survey Master – Best Quiz, Exam and Survey Plugin for WordPress - Reflected Cross-Site Scripting
- Quiz and Survey Master is the easiest WordPress Quiz Plugin which can be used to create engaging content to drive traffic and increase user engagement. Everything from viral quiz, trivia quiz, customer satisfaction surveys to employee surveys. This plugin is the ultimate marketing tool for your website. Active installations: 40,000+
- Recently - Authenticated Stored Cross-Site Scripting
- Let’s face it: WordPress’ default Recent Posts widget does the job as promised but it’s not very flexible. Things like excluding certain entries from the list or displaying recent posts by category can’t be done with the stock Recent Posts widget. Therefore, let me introduce Recently. Active installations: 400+
- WordPress Popular Posts - Authenticated Stored Cross-Site Scripting
- WordPress Popular Posts is a highly customizable widget that displays your most popular posts. Active installations: 200,000+
- WP Hardening – Fix Your WordPress Security - Reflected Cross-Site Scripting via URI
- WP Hardening by Astra Security is a tool which performs a real-time security audit of your website to find missing security best practices. Using our ‘Security Fixer’ you can also fix these with a single click from your WordPress backend. Active installations: 5,000+
- WP Hardening – Fix Your WordPress Security - Reflected Cross-Site Scripting via historyvalue
- WP Hardening by Astra Security is a tool which performs a real-time security audit of your website to find missing security best practices. Using our ‘Security Fixer’ you can also fix these with a single click from your WordPress backend. Active installations: 5,000+
- WP Config File Editor - Authenticated Stored Cross-Site Scripting
- Modify WordPress Memory, Cache, Upgrade, Post, Localization, Cron, Multi Sites, Database, Secure Keys, Debugging, Proxy and Cookies constants values allocated in wp-config.php file using web form or even through Raw Editor. Active installations: 20,000+
- Admin Columns - Authenticated Stored Cross-Site Scripting
- Manage and organize columns in the posts, users, comments and media lists in the WordPress admin panel. Transform the WordPress admin screens into beautiful, clear overviews. Active installations: 100,000+
- WP Google Maps - Authenticated Stored Cross-Site Scripting
- The easiest to use Google Maps and Open Layers Maps plugin! Active installations: 400,000+
- Stripe Payment Gateway for WooCommerce (Credit, Debit Card, Apple Pay, Google Pay, Alipay, Stripe Checkout) - Reflected Cross-Site Scripting
- Do you want to accept credit cards, debit cards, Alipay, Apple Pay, or Google Pay in your WooCommerce store? Stripe Payment Gateway Plugin for WooCommerce lets you accept payments from multiple payment platforms directly on your website via the Stripe Payment Gateway. Active installations: 10,000+
- Smart Slider 3 - Authenticated Stored Cross-Site Scripting
- Smart Slider 3 is the most powerful and intuitive WordPress plugin to create sliders which was never possible before. Fully responsive, SEO optimised and works with any WordPress theme. Create beautiful sliders and tell stories without any code. Active installations: 800,000+
- Welcart e-Commerce - Cross-Site Scripting
- Welcart is a free e-commerce plugin for WordPress with top market share in Japan. Welcart comes with many features and customizations for making an online store. You can easily create your own original online store. Active installations: 20,000+
- WP SVG images - Authenticated Stored Cross-Site Scripting
- Add SVG support to your WordPress web. You can upload SVG files, you can see them as thumbnails in media library, etc. Active installations: 20,000+
- Smooth Scroll Page Up/Down Buttons - Authenticated Stored Cross-Site Scripting
- The Smooth Page Scroll Up/Down Buttons plugin for WordPress adds buttons to every page of your site, that can be used to (smoothly) scroll up or down exactly one screen/page at a time. This can be particularly handy for pages with a lot of text/content, or in cases wherever a browser’s scrollbar is just not good enough (or not present at all, like on tablets) to enable one-click, one-screen scrolling. Active installations: 5,000+
- Request a Quote - Authenticated Stored Cross-Site Scripting
- Request a quote plugin is designed for small business owners to receive request for quotation (RFQ) or request for information (RFI) from customers. Active installations: 2,000+
- WP YouTube Lyte - Authenticated Stored Cross-Site Scripting
- WP YouTube Lyte allows you to “lazy load” your video’s, by inserting responsive “Lite YouTube Embeds”. These look and feel like normal embedded YouTube, but only call the “fat” YouTube-player when clicked on, thereby reducing download size & rendering time substantially when embedding YouTube occasionally and improving page performance dramatically when you’ve got multiple YouTube video’s on one and the same page. Active installations: 30,000+
- JobSearch WP Job Board WordPress Plugin - Authenticated Stored Cross-Site Scripting
- WP Job Search brings you the most simple solution to display jobs on any type of websites. You may already know, some really big Job Portals provides the option to use their database and extend your website with job offers. This plugin can make everything automatically, some job providers also pay commission when any of your visitors click on the job links.
- WP Reset – Most Advanced WordPress Reset Tool - Authenticated Stored Cross-Site Scripting
- WP Reset quickly resets the site’s database to the default installation values without modifying any files. It deletes all customizations and content, or just chosen parts like theme settings. WP Reset is fast and safe to use thanks to the built-in snapshots which provide 1-click restore functionality. Active installations: 300,000+
- Backup by 10Web - Reflected Cross-Site Scripting
- This plugin has been closed as of June 2, 2022 and is not available for download. This closure is permanent.
- W3 Total Cache - Authenticated Stored Cross-Site Scripting
- W3 Total Cache (W3TC) improves the SEO and user experience of your site by increasing website performance and reducing load times by leveraging features like content delivery network (CDN) integration and the latest best practices. Active installations: 1+ million
- Contact Form Plugin – Fastest Contact Form Builder Plugin for WordPress by Fluent Forms - Cross-Site Request Forgery
- WP Fluent Forms is the ultimate user-friendly, customizable drag-and-drop WordPress Contact Form Plugin that offers you all the premium features, plus many more completely unique additional features. A perfect WordPress Form builder plugin should be developed in a way, so that you don’t have to code every time you need to integrate a form in your website, but can be set up in minutes. And that’s why, we have developed WP Fluent Forms for you. Active installations: 90,000+
- Advanced AJAX Product Filters - Unauthenticated Reflected Cross-Site Scripting
- WooCommerce AJAX Product Filters – Advanced product filtering ability for your WooCommerce shop. Add unlimited filters with one widget. Active installations: 50,000+
- Browser Screenshots - Stored Cross-Site Scripting
- Use the "browser-shot" shortcode to automate the process of taking website screenshots. An icon is also added to the TinyMCE editor to make the shortcode creation process easy. Active installations: 6,000+
- Sign-up Sheets - Authenticated Stored Cross-Site Scripting
- This plugin lets you quickly and easily setup sign-up sheets on your WordPress site. Active installations: 1,000+
- Prismatic - Reflected Cross-Site Scripting
- Display beautiful code snippets with Prism.js, Highlight.js, or plain code escaping. Active installations: 2,000+
- Prismatic - Stored Cross-Site Scripting
- Display beautiful code snippets with Prism.js, Highlight.js, or plain code escaping. Active installations: 2,000+
- Glass - CSRF to Stored Cross-Site Scripting
- This plugin has been closed as of May 26, 2022 and is not available for download. This closure is temporary, pending a full review.
- Simple Sort&Search - Stored Cross-Site Scripting
- This plugin has been closed as of May 19, 2022 and is not available for download. This closure is temporary, pending a full review.
- Salon booking system - Unauthenticated Stored Cross-Site Scripting
- Salon Booking System is a complete and easy to manage appointments scheduling system to help your business getting more reservations on your website and saving a lot of time with your agenda management tasks. Active installations: 8,000+
- YOP Poll - Unauthenticated Stored Cross-Site Scripting
- YOP Poll plugin allows you to easily integrate a survey in your blog post/page and to manage the polls from within your WordPress dashboard but if offers so much more than other similar products. Simply put, it doesn’t lose sight of your needs and ensures that no detail is left unaccounted for. Active installations: 20,000+
- CiviCRM - CSRF to Stored Cross-Site Scripting
- CiviCRM is an open source project that produces software for nonprofit and civic sector organizations. CiviCRM, the software, is a web-based, highly customizable CRM released under the GNU Affero General Public License version 3 (GNU AGPL v3). CiviCRM is used by a diverse range of organizations around the world and translated into dozens of languages.
Stay Healthy! A healthier online business starts today and it begins with you. Hire security experts to solve all your XSS JUN 2021 issues.
BRIEF: Cross-Site Scripting JUN 2021 is a type of security vulnerability typically found in web applications. XSS attacks enable attackers to inject client-side scripts into web pages viewed by other users. A cross-site scripting vulnerability may be used by attackers to bypass access controls such as the same-origin policy.
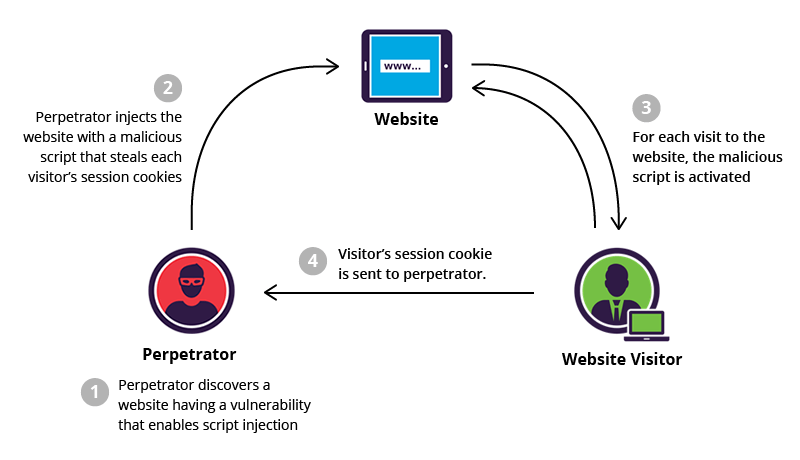
What is Cross-Site Scripting JUN 2021?
Cross-Site Scripting (XSS) attacks are a type of injection, in which malicious scripts are injected into otherwise benign and trusted websites. XSS attacks occur when an attacker uses a web application to send malicious code, generally in the form of a browser side script, to a different end user. Flaws that allow these attacks to succeed are quite widespread and occur anywhere a web application uses input from a user within the output it generates without validating or encoding it.
An attacker can use XSS to send a malicious script to an unsuspecting user. The end user’s browser has no way to know that the script should not be trusted, and will execute the script. Because it thinks the script came from a trusted source, the malicious script can access any cookies, session tokens, or other sensitive information retained by the browser and used with that site. These scripts can even rewrite the content of the HTML page.
What is the impact of a XSS JUN 2021 attack?
The actual impact of an XSS attack generally depends on the nature of the application, its functionality and data, and the status of the compromised user. For example:
- In a simple public application, where all users are anonymous and all information is public, the impact will often be minimal. Nothing else to steal.
- In an application holding sensitive or private/personal data, such as banking transactions, emails, or healthcare records, the impact will usually be serious.
- If the compromised user has elevated privileges within the application, then the impact will generally be critical, allowing the attacker to take full control of the vulnerable application and compromise all users, owners and their data.
What kind of XSS attacks are exploited?
- Reflected XSS, where the malicious script comes from the current HTTP request.
- Stored XSS, where the malicious script comes from the website's database.
- DOM-based XSS, where the vulnerability exists in client-side code rather than server-side code.
CONTACT US TODAY with any reported XSS JUN 2021 vulnerability! Do you suspect any Cross-Site Scripting in your WordPress?
Do you suspect any Cross-Site Scripting within your WordPress? Contact us today for a free scan!
We’re passionate about helping you grow and make your impact
Continue being informed
Monthly vulnerability reports about WordPress and WooCommerce, plugins, themes.
Weekly inspiration, news and occasional with hand-picked deals. Unsubscribe anytime.


