
WP XSS JAN 2024
WP Cross-Site Scripting JAN 2024
Managed WP & Woo Security Report
Be informed about the latest WP Cross-Site Scripting JAN 2024, identified and reported publicly. WP XSS JAN 2024 is a -39% DECREASE compared to previous month. Consider for your online safety, a managed WP/Woo security AUDIT, – OR – switching with a TOP10LIST alternative WP Security Plugin – OR – Hire us for your recurrent needs of managed WordPress Security and managed WooCommerce Security. The following cases made headlines PUBLICLY just last month in the WP XSS JAN 2024 & WP Cross-Site Scripting JAN 2024 category:
WHO needs managed WP security? EVERYBODY!
Today's reality needs a Web Application Firewall (WAF) plus an Intrusion Prevention System (IPS) to mitigate "gazillion" different threats in your WordPress. Get your WP Cross-Site Scripting JAN 2024 Patch Management.
| WordPress Cross-Site Scripting (XSS) reported in 2023: | 2928 |
| WordPress Cross-Site Scripting (XSS) reported in 2024: | 135 |
WHO needs managed WP Maintenance? EVERYBODY!
Today’s reality requires daily clean-ups with database optimisations, weekly updates and upgrades for both free & premium modules, plus the occasional emergency changes when critical vulnerabilities are publicly disclosed without patches. Order WP Cross-Site Scripting JAN 2024 Patch Management.
BRIEF: WP Cross-Site Scripting JAN 2024 is a type of security vulnerability typically found in web applications. XSS attacks enable attackers to inject client-side scripts into web pages viewed by other users. A cross-site scripting vulnerability may be used by attackers to bypass access controls such as the same-origin policy.
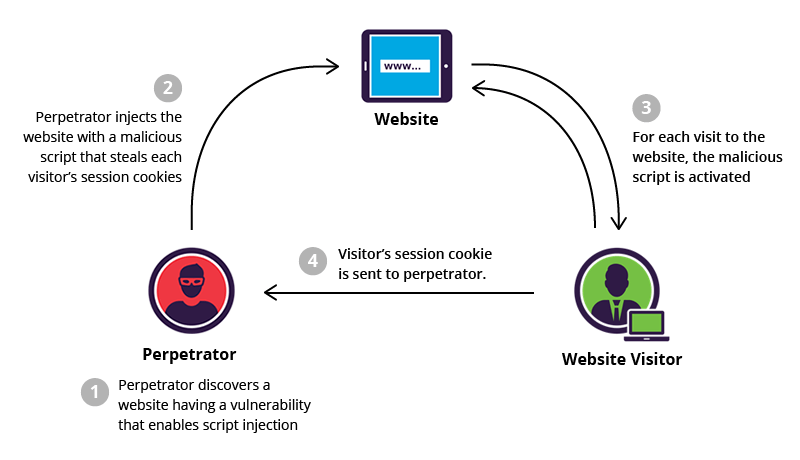
What is WP Cross-Site Scripting JAN 2024?
Cross-Site Scripting (XSS) attacks are a type of injection, in which malicious scripts are injected into otherwise benign and trusted websites. XSS attacks occur when an attacker uses a web application to send malicious code, generally in the form of a browser side script, to a different end user. Flaws that allow these attacks to succeed are quite widespread and occur anywhere a web application uses input from a user within the output it generates without validating or encoding it.
An attacker can use XSS to send a malicious script to an unsuspecting user. The end user’s browser has no way to know that the script should not be trusted, and will execute the script. Because it thinks the script came from a trusted source, the malicious script can access any cookies, session tokens, or other sensitive information retained by the browser and used with that site. These scripts can even rewrite the content of the HTML page.
What is the impact of a WP XSS JAN 2024 attack?
The actual impact of an XSS attack generally depends on the nature of the application, its functionality and data, and the status of the compromised user. For example:
- In a simple public application, where all users are anonymous and all information is public, the impact will often be minimal. Nothing else to steal.
- In an application holding sensitive or private/personal data, such as banking transactions, emails, or healthcare records, the impact will usually be serious.
- If the compromised user has elevated privileges within the application, then the impact will generally be critical, allowing the attacker to take full control of the vulnerable application and compromise all users, owners and their data.
What kind of XSS attacks are exploited?
- Reflected XSS, where the malicious script comes from the current HTTP request.
- Stored XSS, where the malicious script comes from the website's database.
- DOM-based XSS, where the vulnerability exists in client-side code rather than server-side code.
Security is not a single-task job
Need managed WP Security and got no clue where to start? Hire an expert. Pay a coffee per week, its cheaper than 1 hour for a freelancer.
Not sure that our recurrent security offer is worthy of long-term consideration? Contact us today for a Cross-Site Scripting audit! Decide after you compare RISK + IMPACT versus COST.
We’re passionate about helping you grow and make your impact
Continue being informed
Monthly vulnerability reports about WordPress and WooCommerce, plugins, themes.
Weekly inspiration, news and occasional with hand-picked deals. Unsubscribe anytime.


