SQL Injections MAY 2022
Managed WordPress Security Report
Be informed about the latest SQL Injections MAY 2022, identified and reported publicly. As these SQL Injections MAY 2022 vulnerabilities have a severe negative impact on any WordPress Security, consider our security audit.
An estimated 302.600+ active WordPress installations are susceptible to this attack type, considering only the publicly available numbers. It is a slight -6% decrease compared to last month. The estimated number can increase by 20-25% with premium versions as they are private purchases.
Furthermore, the initial estimation can multiply if we consider the already patched versions BUT NOT UPDATED by owners, as the vulnerability remains active within their domain. As these owners start changing their hosting provider (due to constant unexplained issues), they actively migrate these vulnerabilities behind protected areas, possibly exposing other clean WP to different attack types.
The following cases made headlines PUBLICLY in the SQL Injections MAY 2022 category:
Hire security geeks to protect your WP/Woo from publicly reported cases of SQL Injections MAY 2022 BEFORE IT’S TOO LATE! You will also protect your customers, your reputation and your online business!
- OOPSpam Anti-Spam - SQL Injection (SQLi)
- Active installations: 50+
- Documentor – Create Product Documentation - Unauthenticated SQL Injection (SQLi)
- This plugin has been closed as of March 29, 2022 and is not available for download. This closure is temporary, pending a full review.
- Photo Gallery by 10Web – Mobile-Friendly Image Gallery - Reflected Cross-Site Scripting (XSS)
- Photo Gallery by 10Web – Mobile-Friendly Image Gallery - Unauthenticated SQL Injection (SQLi)
- Active installations: 300,000+
- Multiple Shipping Address Woocommerce - Unauthenticated SQL Injection (SQLi)
- Active installations: 900+
- SiteSuperCharger - Unauthenticated SQL Injection (SQLi)
- Active installations: 300+
- Order Listener for WooCommerce – Play Sounds Instantly on New Orders - Unauthenticated SQL Injection (SQLi)
- Active installations: 300+
- BadgeOS - Unauthenticated SQL Injection (SQLi)
- This plugin has been closed as of March 29, 2022 and is not available for download. This closure is temporary, pending a full review.
- SEMA API - Unauthenticated SQL Injection (SQLi)
- This plugin has been closed as of March 3, 2022 and is not available for download. This closure is temporary, pending a full review.
- Product Filter For WooCommerce Product - Unauthenticated SQL Injection (SQLi)
- This plugin has been closed as of March 29, 2022 and is not available for download. This closure is temporary, pending a full review.
- Personal Dictionary - Unauthenticated SQL Injection (SQLi)
- Active installations: 20+
- Ubigeo de Perú para Woocommerce y WordPress - Unauthenticated SQL Injection (SQLi)
- Active installations: 1,000+
- #1 Killer WordPress Map Plugin - Unauthenticated SQL Injection (SQLi)
- Active installations: N/A
- 3xSocializer - Authenticated SQL Injection (SQLi)
- This plugin has been closed as of April 25, 2022 and is not available for download. This closure is temporary, pending a full review.
- RSVPMaker - Unauthenticated SQL Injection (SQLi)
- Active installations: 600+
- Hermit 音乐播放器 - Cross-Site Request Forgery (CSRF) leading to Stored Cross-Site Scripting (XSS)
- Hermit 音乐播放器 - Multiple Cross-Site Request Forgery (CSRF)
- Hermit 音乐播放器 - Unauthenticated SQL Injection SQLi)
- Hermit 音乐播放器 - Authenticated SQL Injection (SQLi)
- This plugin has been closed as of April 25, 2022 and is not available for download. This closure is temporary, pending a full review.
Get Healthy, Stay Healthy! A healthier online business starts today and it begins with your WP/Woo. Hire security experts to solve all your vulnerabilities created from SQL Injections MAY 2022.
BRIEF: SQL Injections MAY 2022 is a code injection technique, used to attack data-driven applications, in which malicious SQL statements are inserted into an entry field for execution.
What is SQL Injections MAY 2022?
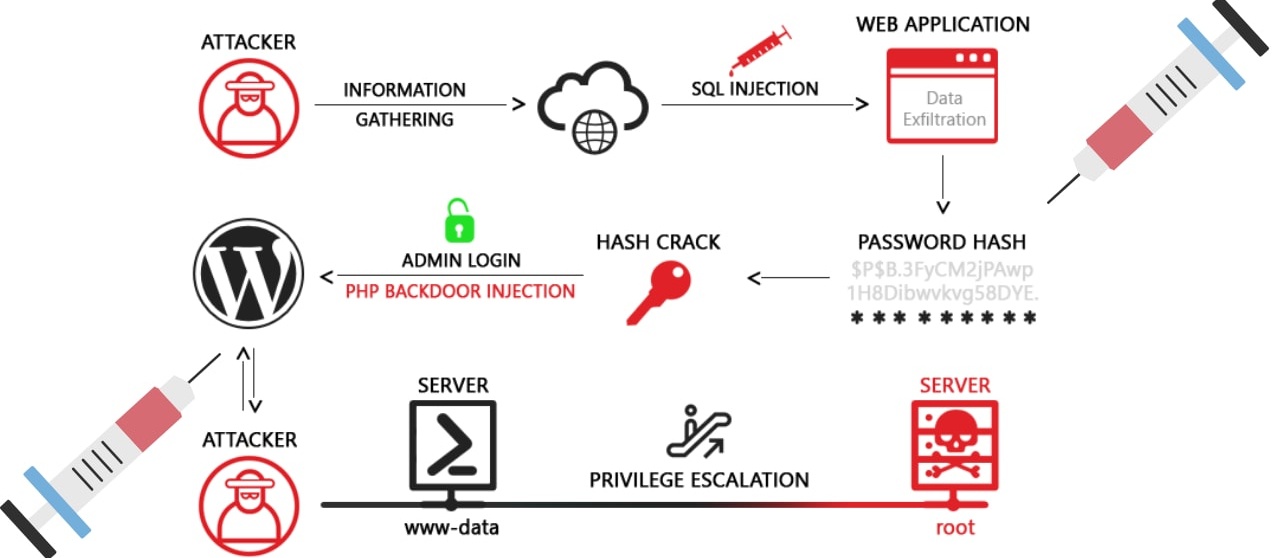
SQL injection is a web security vulnerability that allows an attacker to interfere with the queries that an application makes to its database. It generally allows an attacker to view data that they are not normally able to retrieve. This might include data belonging to other users, or any other data that the application itself is able to access.
In many cases, an attacker can modify or delete this data, causing persistent changes to the application's content or behaviour. In some situations, an attacker can escalate an SQL injection attack to compromise the underlying server or other back-end infrastructure, or perform a denial-of-service attack.
What is the impact of an SQL Injections MAY 2022?
A successful SQL injection attack can result in unauthorised access to sensitive data, such as passwords, credit card details, or personal user information. Many high-profile data breaches in recent years have been the result of SQL injection attacks, leading to reputational damage and regulatory fines. In some cases, an attacker can obtain a persistent backdoor into an organisation's systems, leading to a long-term compromise that can go unnoticed for an extended period.
What kind of SQL Injections are exploited?
There are a wide variety of SQL injection vulnerabilities, attacks, and techniques, which arise in different situations. Some common SQL injection examples include:
- Retrieving hidden data, where you can modify an SQL query to return additional results.
- Subverting application logic, where you can change a query to interfere with the application's logic.
- UNION attacks, where you can retrieve data from different database tables.
- Examining the database, where you can extract information about the version and structure of the database.
- Blind SQL injection, where the results of a query you control are not returned in the application's responses.
SOLVE TODAY any reported SQL Injections MAY 2022 vulnerability! Do you suspect any SQL Injections in your WordPress / WooCommerce?
Not sure that our recurrent security offer is worthy of long-term consideration? Contact us today for an SQL Injections audit! Decide after you compare RISK + IMPACT versus COST.
We’re passionate about helping you grow and make your impact
Continue being informed
Monthly vulnerability reports about WordPress and WooCommerce, plugins, themes.
Weekly inspiration, news and occasional with hand-picked deals. Unsubscribe anytime.