
Social engineering approaches further matured in both phishing and malware attacks, with increased geotargeted malware attacks. For all the known WordPress Security issues, these were the most identified types:
- BANKING TROJANS: This type of malware steals victims bank login credentials, usually by redirecting victims’ browser to a fake version of their bank’s website browsers or injecting fake login forms into the real site.
- WEBINJECTS: A technique that alters Web pages as they are displayed to the users. Attackers use WEBINJECTS to append insecure forms to seemingly secure websites. When users fill out the forms (say, with their banking credentials), that information is sent to the attacker instead of the bank.
- CREDENTIAL PHISHING: A type of phishing that tries to trick users into providing account credentials such as usernames and passwords.
- DYNAMIC DATA EXCHANGE: DDE is a 20-year-old communications protocol in Microsoft Windows that allows documents to pull information from other documents. The technique has been largely replaced by newer protocols but is still supported in Windows.
- RANSOMWARE: This type of malware locks away victims’ data by encrypting it, then demands a “ransom” to unlock it with a decryption key.
- CRIMEWARE: This term encompasses a wide range of malware used for cybercrime such as stealing credit card numbers, raiding online bank accounts, corporate intellectual property theft and more.
- INFORMATION STEALERS: Malware used to collect information from compromised systems and send it to the attacker. Keyloggers, which record users’ keystrokes (hoping they will type their usernames, passwords, credit card numbers, and so on), are a common type.
- DOWNLOADER: Downloaders are snippets of code or scripts used to gain a foothold on a targeted system and download other malware components.
Our only security is our ability to change. ~ John Lilly
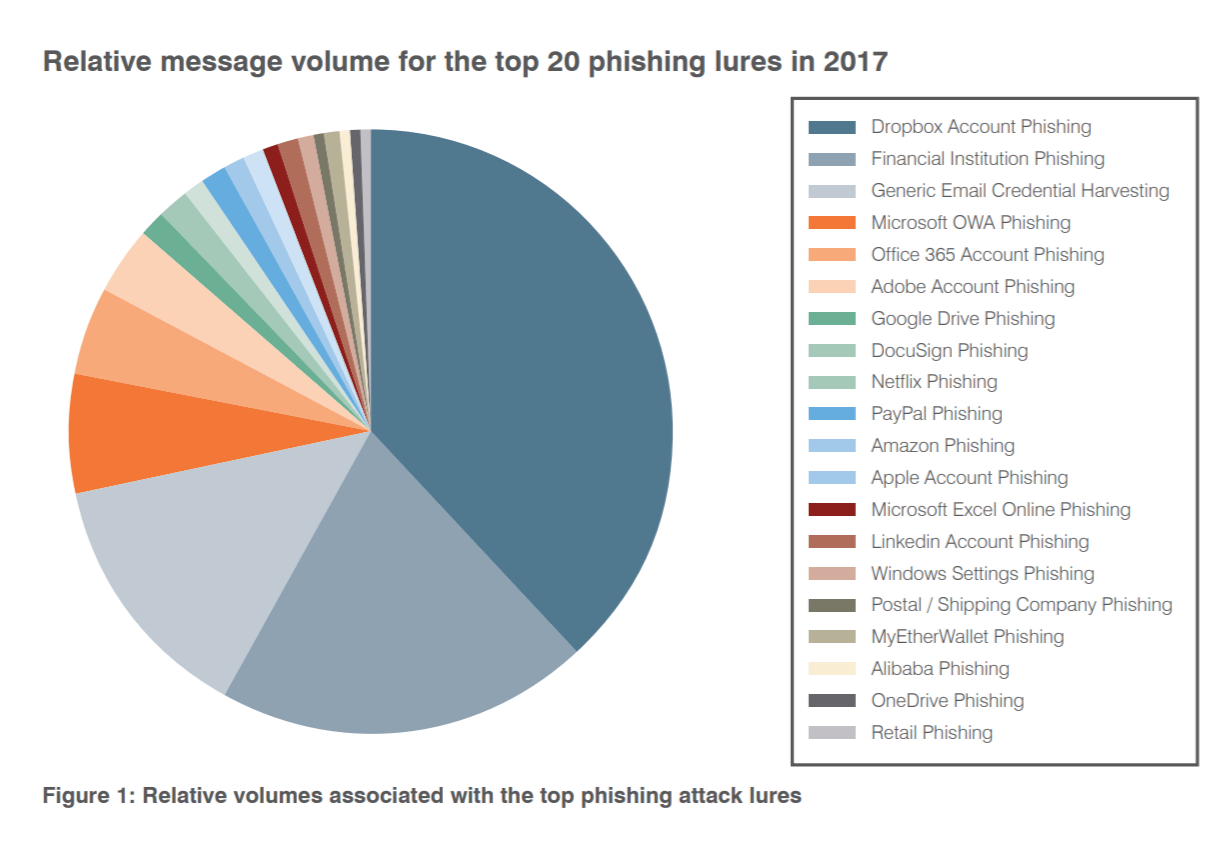
The volume of threats does not always equate their effectiveness. Threat actors often compensate for less effective but potentially more lucrative lures with volume. By the same token, lures more likely to generate a higher percentage of clicks may not need large campaigns. The relative volumes for the top 20 CREDENTIAL PHISHING lure in 2017 are:
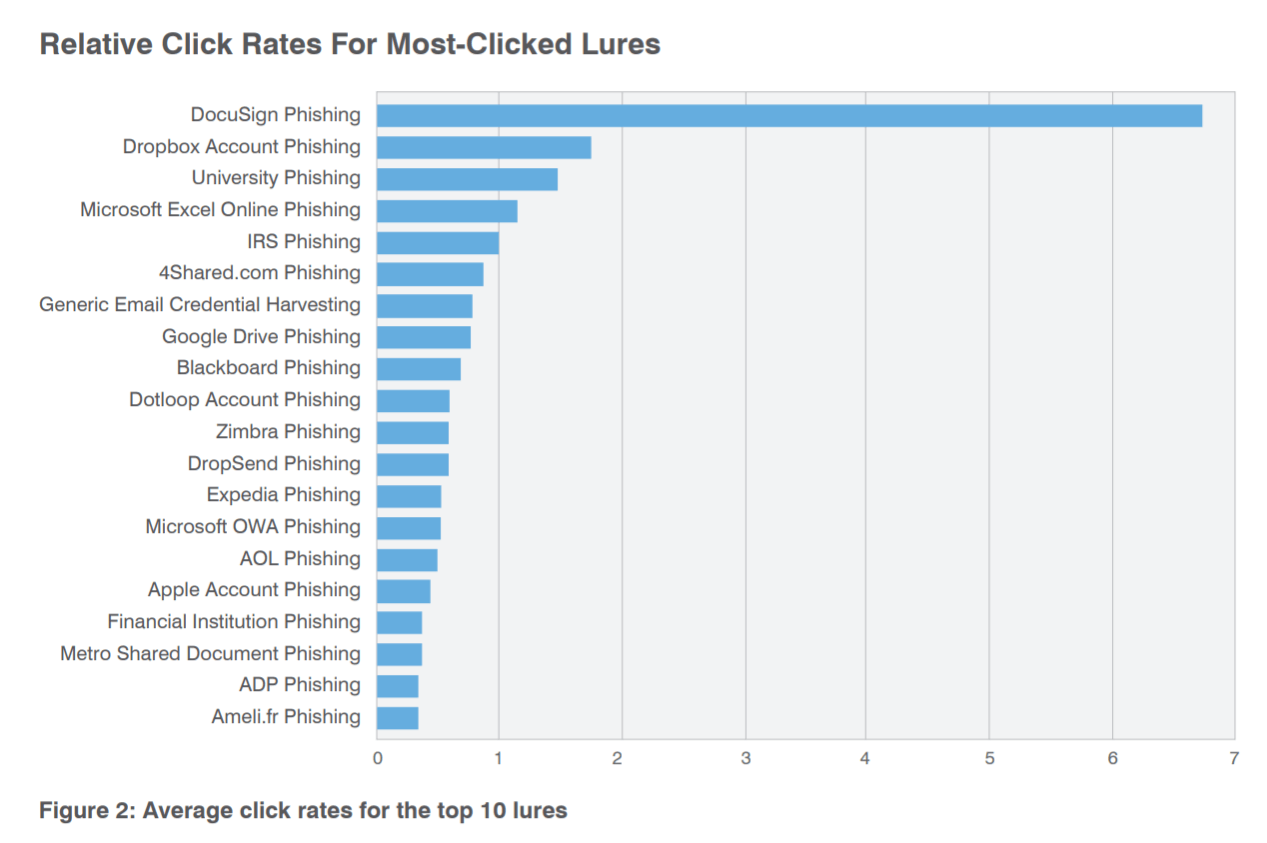
Click rates also vary by industry, with predictable trends based on likely user profiles and use cases.
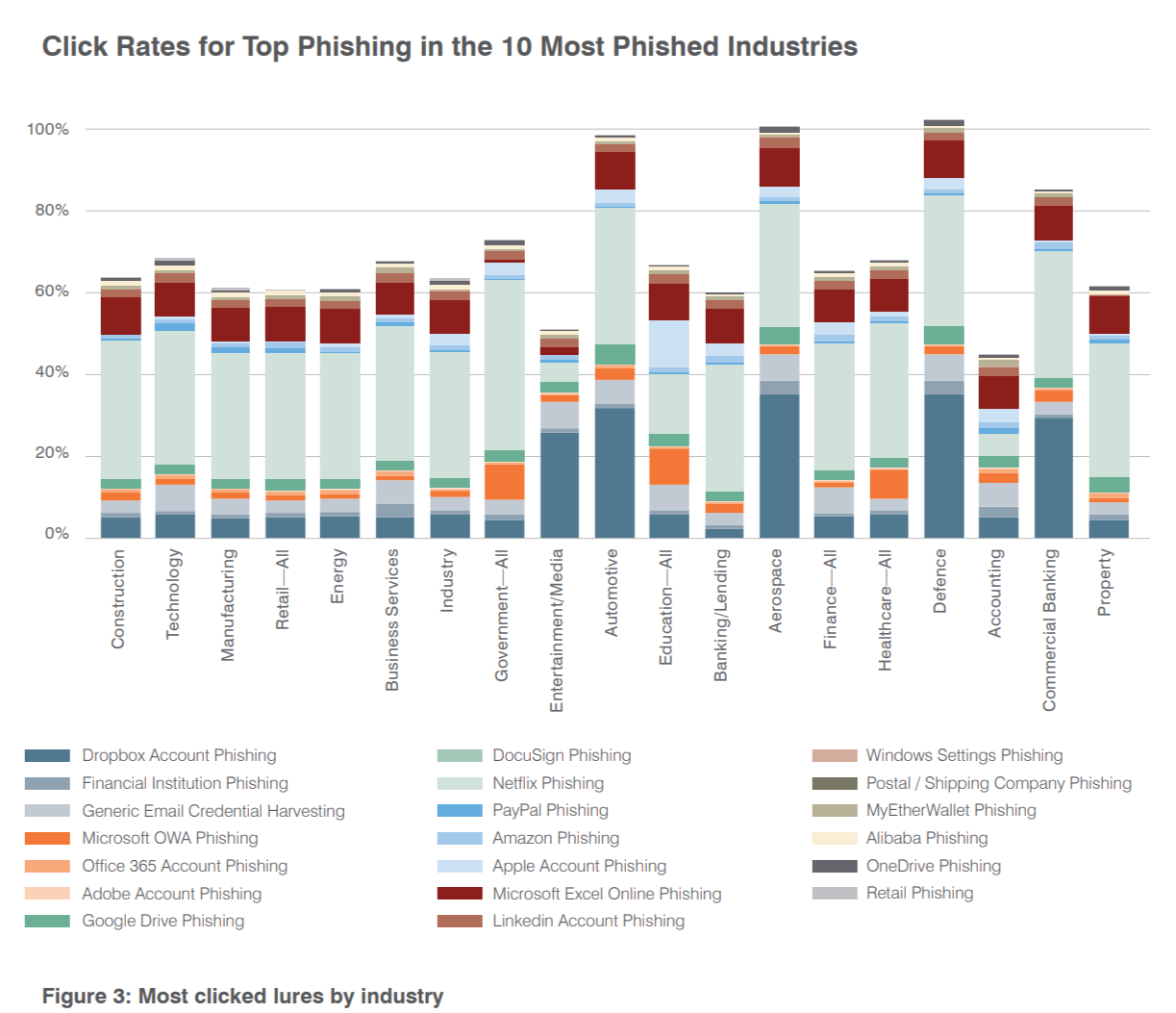
While the volume of phishing threats was consistent across industries, click rates were highest in automotive, aerospace, defence and commercial banking. These industries were associated with very high Dropbox click rates. DocuSign click rates were generally high across the board with notable exceptions such as education.
At the end of the day, the goals are simple: safety and security. ~ Jodi Rell
Overall use of malicious attachments—ranging from compressed script files to exploit documents—exceeded
URLs by almost 28%. Figure 4 breaks down the differences in aggregated malicious attachments vs malicious URLs in email campaigns by malware family.
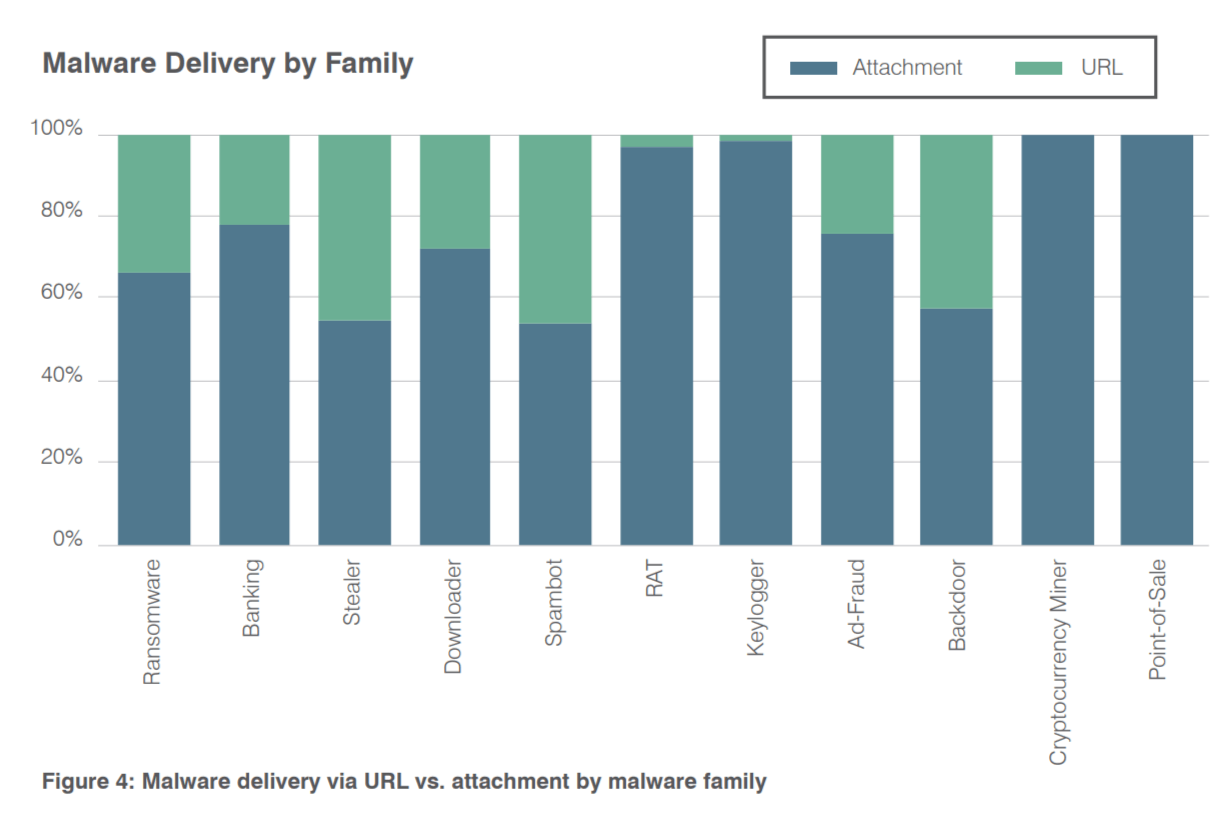
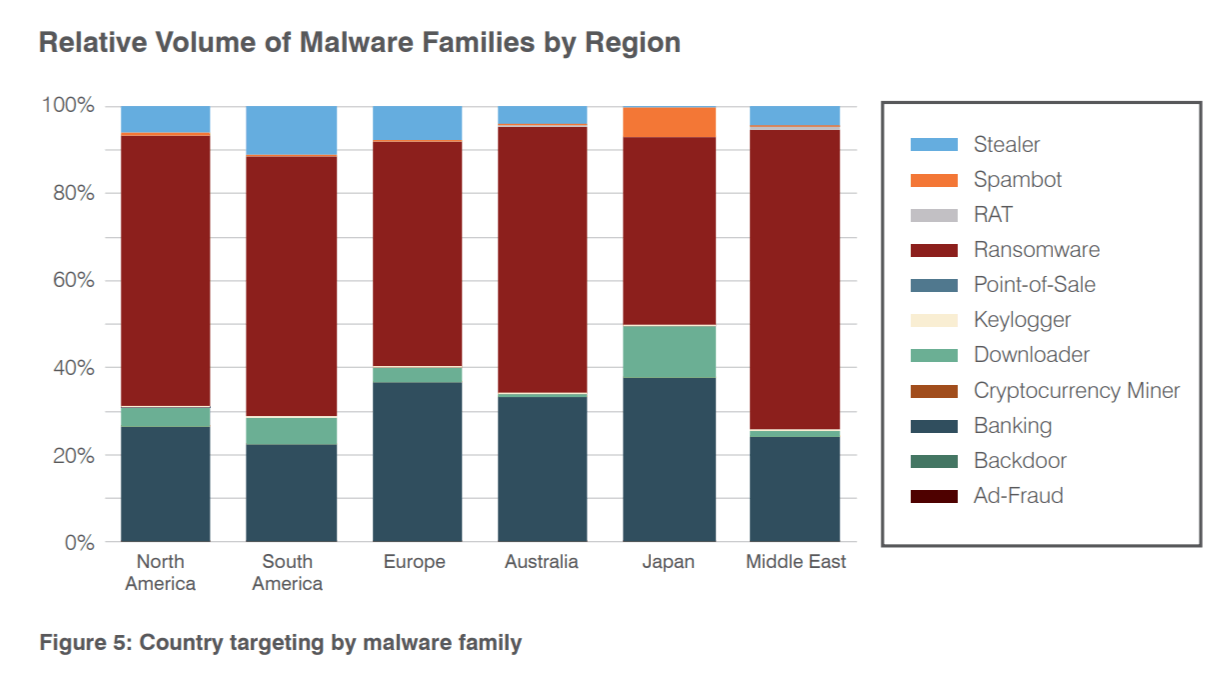
RANSOMWARE predominated worldwide in 2017. But banking Trojans appeared in more than 30% of malicious emails in Europe, Japan and Australia.
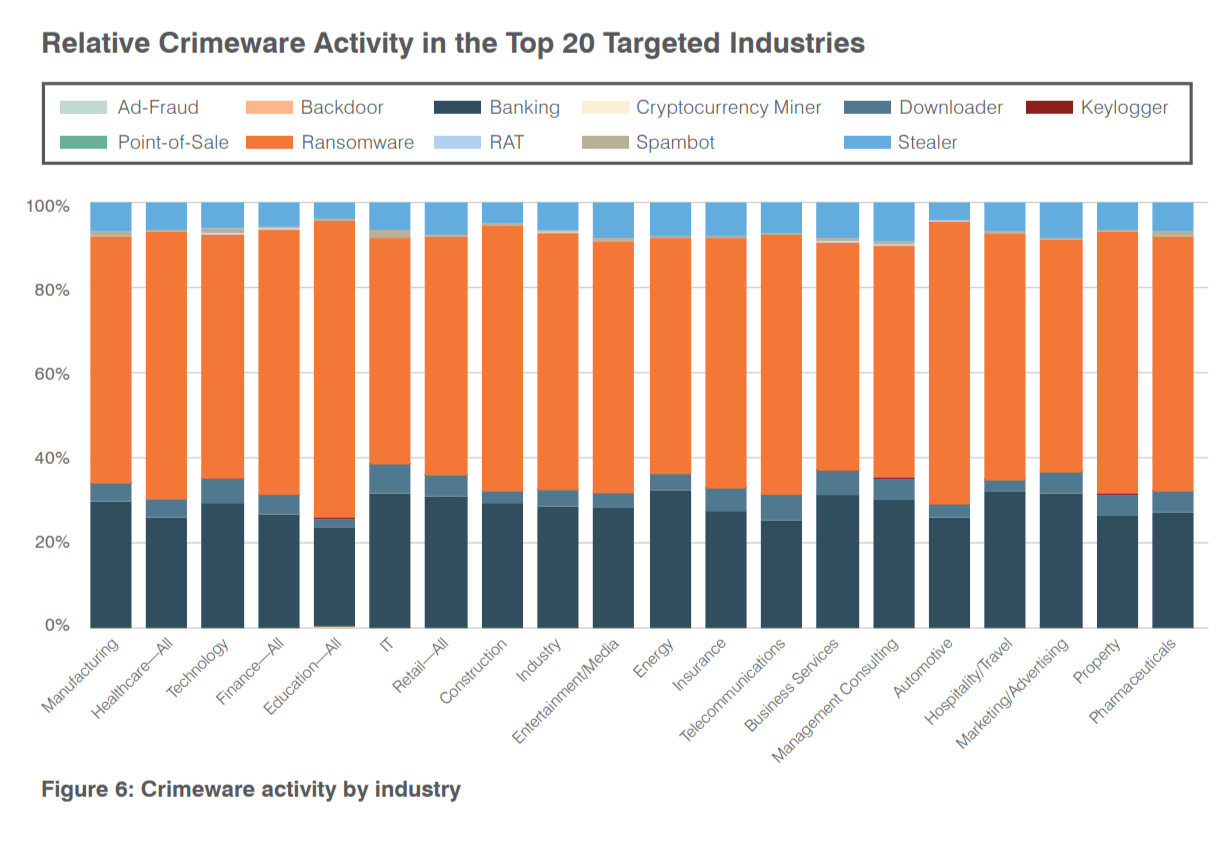
CRIMEWARE activity varied by industry, with a few standout trends. No industries escaped attacks. Malware families included:
Protect your WordPress: BEFORE IT'S TOO LATE! You will also protect your customers, your reputation and your online business!
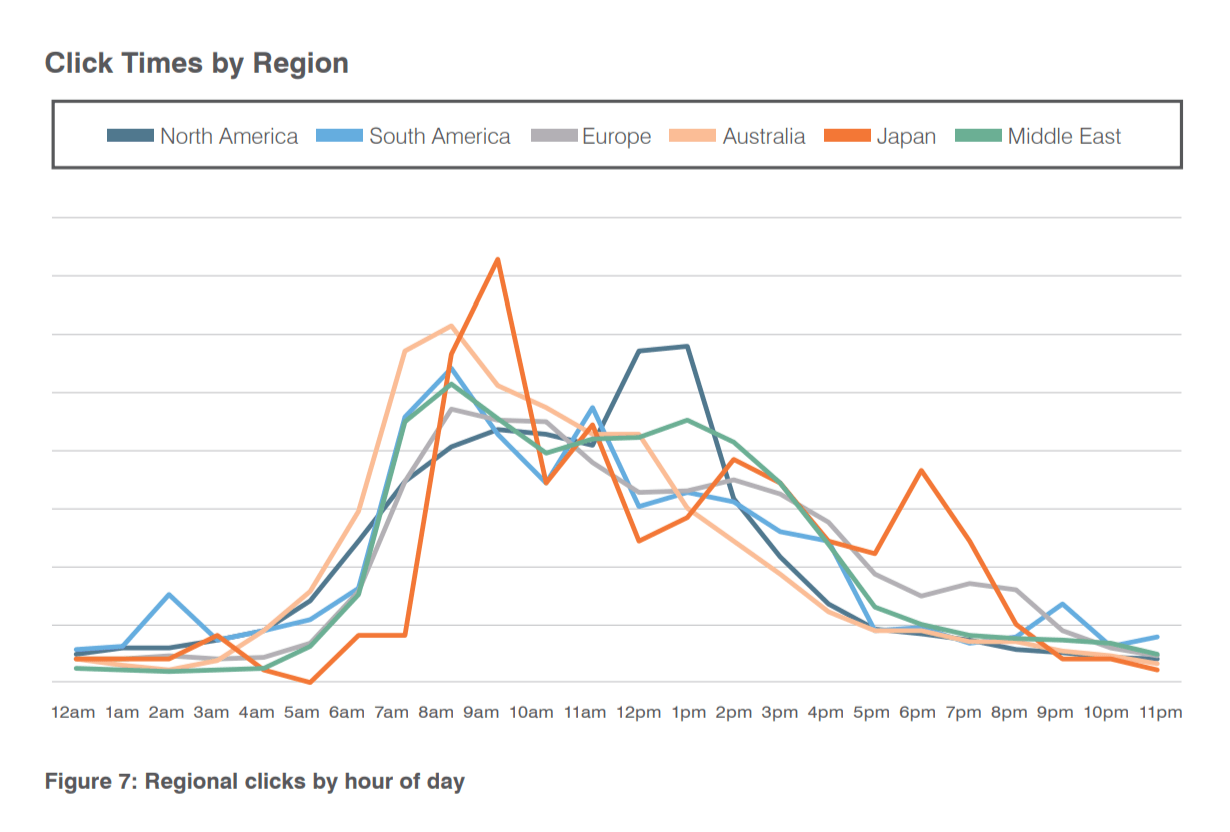
When examined how people behaved in response to these threats, regional differences uncovered that can help defenders deploy the right resources at the right time. Figure 7 shows that North American employees tended to click around three-time windows: the
beginning of the workday, lunch, and the end of the workday.
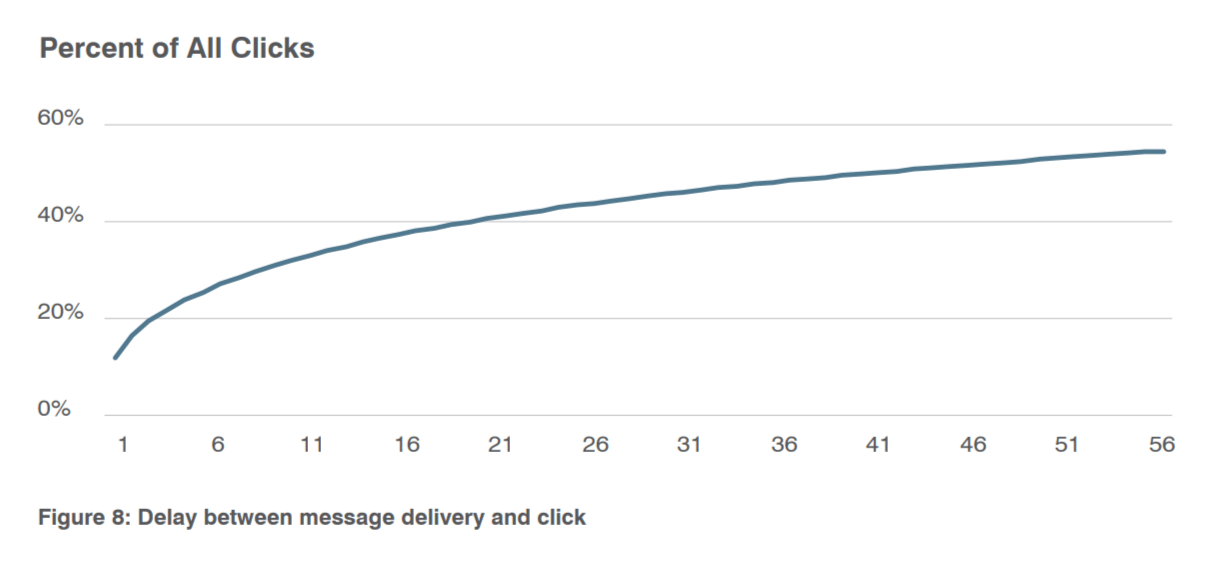
Despite these regional differences, 52% of clicks occurred within one hour of the message being delivered. Figure 8 shows that delays between delivery and click follow a nearly logarithmic curve — clicks taper off sharply after delivery of malicious messages.
Get Healthy, Stay Healthy: A healthier online business starts today and it begins with you!
We're passionate about helping you grow and make your impact
Continue being informed
Monthly vulnerability reports about WordPress and WooCommerce, plugins, themes.
Weekly inspiration, news and occasional with hand-picked deals. Unsubscribe anytime.








