Attackers have relied more and more on social engineering to trick users into revealing credentials, installing malware or wiring funds. Few of us are still tempted to send money to distressed Nigerian princes anymore. But the basic principles behind those early email scams are alive and well. We see them in large malicious email campaigns, Web-based attacks, on social media, in email fraud and elsewhere.
Businesses have improved their system-patching regimens. They have rolled out new WP security tools and have deployed layered defences across networks and endpoints. So why is WordPress Security breaches still a problem? Because cybersecurity is not strictly an IT and operations issue. As recent headline-grabbing attacks have shown, it goes far beyond the back office. In today’s threat landscape, information security has a number of distinctly human elements. And as exploiting software and hardware vulnerabilities grows more difficult, attackers are turning to people. Human nature is the vulnerability. Even the best defences can be thwarted by one wayward click on a link or attachment or one innocent response to a well-crafted email lure. People remain the weakest link in the WordPress Security chain, a fact not lost on cybercriminals.
Today, social engineering tends to take one of two forms:
• Simple lures used in large campaigns. These may simply be file names for malicious attached documents, such as “resume.doc” or “invoice.xls.” Only a small fraction (among hundreds of thousands or millions of recipients) will be curious enough to open them.
• Highly sophisticated, persuasive schemes designed to generate a higher response rate. These use precisely-rendered graphics and stolen branding or create well-crafted email lures and fake documents that appear legitimate. The latter is more likely to appear in smaller, more targeted attacks, but we are seeing even larger campaigns and Web-based social engineering schemes that create very convincing collateral.
Several tactics fall under the umbrella of social engineering:
• Conveying a sense of urgency
• Replicating trusted brands
• Preying on our natural curiosity
• Taking advantage of conditioned responses to frequent events such as software updates
Our only security is our ability to change. ~ John Lilly
These techniques work every day. Users click, install and reply without threat actors needing to develop expensive and short-lived EXPLOITS. An EXPLOIT type attack is a software or hardware vulnerability, PUBLICLY KNOWN, that hasn’t been fixed (unpatched) with an update.
Many threat actors who used to invest time and resources in creating automated exploits have turned to brand theft instead. Brand-theft is a highly effective means of tricking users into believing they are interacting with legitimate sites and services. This kind of attack uses professional-grade graphics and strategic TYPOSQUATTING that can fool even security-conscious users. Typosquatting goes hand-in-hand with brand-theft. Attackers register Web domains similar to those owned and used by legitimate brands. Typosquatting allows cybercriminals to send emails from what seems to be a trusted brand and direct victims to a website that looks like the real thing.
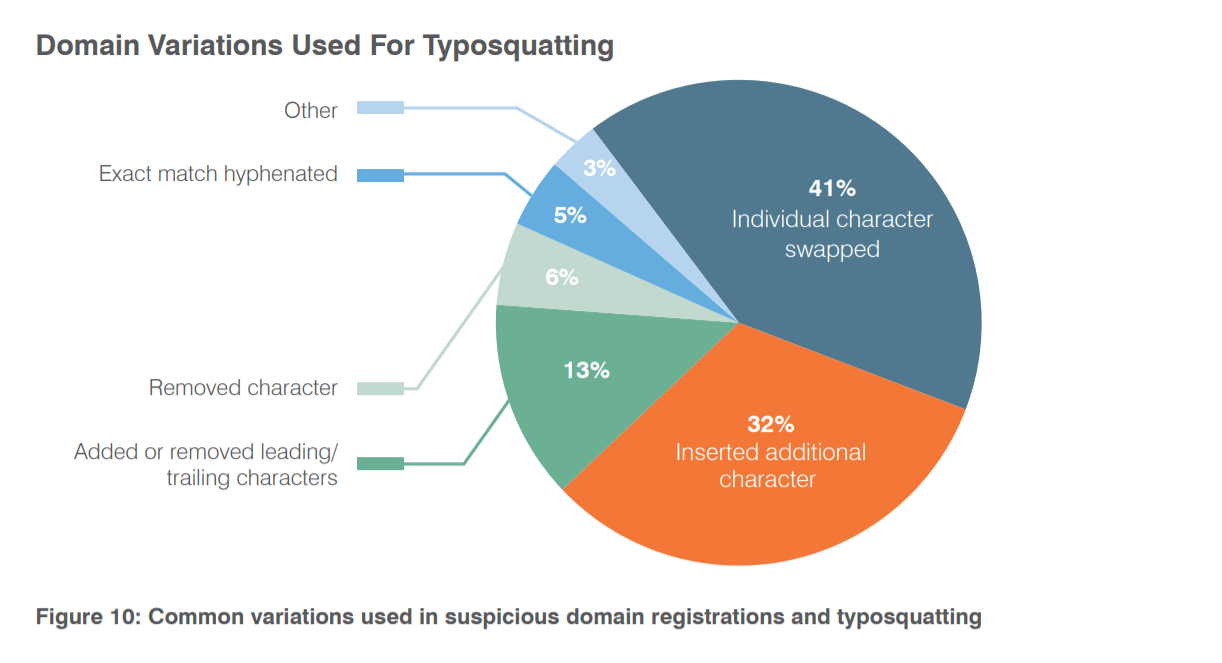
TYPOSQUATTING means Fraudsters register domains that are misspellings or typographically mangled versions of a legitimate domain to trick users who mistype the URL or do not look closely at email headers. For large enterprises, suspiciously registered domains can outnumber brand-registered domains 20 to 1.
At the end of the day, the goals are simple: safety and security. ~ Jodi Rell
This wide gap between suspicious and defensive registrations leaves brands open to fraud, phishing, SPOOFING and more. SPOOFING means a technique to trick workers, partners and customers by using email and Web addresses that look like those of trusted brands. Even savvy users may click on links and respond to phishing scams when typosquatting is involved. Most often, threat actors simply swap an individual character. They might register “myc0mpany.com” (using the numeral 0 in place of the letter O) to fool customers and employees of “mycompany.com”.
Threat actors are registering suspicious domains by the score. The 2018 Winter Olympics in Pyeongchang, South Korea, and the 2020 Summer Olympics in Tokyo, Japan, provide a few high-profile examples of suspicious domain registrations. Since 2010, the year the official site of https://www.olympic.org/pyeongchang-2018 was registered, more than 100 similar domains have been registered. Of those, only three were legitimate (though unofficial) domains related to medal-tracking. We have seen similar trends for the upcoming 2020 games. In most cases, the sites have been registered by unauthorised ticket sellers, streaming sites, and more—all intended to capitalise on interest related to the games. Lookalike domains are only part of the picture. Attackers also use polished graphics and familiar visuals to hijack consumers’ trust in popular brands.
Brand theft can extend to phishing schemes for financial institutions, media sites, and even targeted, state-sponsored attacks. The practice has become pervasive. And attackers have grown adept at it, making it difficult for users to distinguish scams from legitimate marketing.
We often talk about “the human factor” in contrast to automated exploits—fully automated exploits such as malvertising and other Web-based attacks that have not relied on human interaction. That distinction is getting fuzzier. In the wake of plunging traffic to automated exploit kits, as many as 95% of Web-based attacks now incorporate social engineering. They may offer users fake updates, bogus WordPress Security alerts or other tricks to persuade users to download and install malware. And for document exploits more common in email attacks, recipients still need to be convinced to open the file. Even last year’s WannaCry and NotPetya attacks exploited vulnerabilities that had available patches.
Exploits are not going away. But all signs point to the human factor as the main component in most attacks going forward. Malicious macros and attached scripts (which require someone to click) will dominate most email-based attacks. And more Web-based attacks will use social engineering. The human factor is simply more reliable—and therefore more lucrative—for attackers.
Protect your WordPress: BEFORE IT'S TOO LATE! You will also protect your customers, your reputation and your online business!
EMAIL FRAUD: THE ULTIMATE HUMAN EXPLOIT?
Email fraud, also known as business email compromise (BEC), arguably relies more on the human factor than any other kind of cyber attack. It uses no malware; it incorporates social engineering, and it often uses out-of-band communications between the attacker and target to add a veneer of legitimacy and evade detection. All of these elements are designed to thwart WordPress Security tools and persuade recipients to transfer funds or send sensitive data—rather than install malware.
Companies of all sizes are about as equally likely to be targeted by an email fraud attack. But some industries were clearly in the sights of attackers. Education was the most-targeted vertical, with four times as many attacks per organisation than average (across all industries). Education also saw the largest year-over-year increase; the average number of attacks per institution jumped 120% vs the previous year’s average. Management consulting, entertainment/media and telecommunications were the four most targeted sectors.
Seemingly natural targets for cybercrime, such as the defence and aerospace industries, ranked near the bottom of the list. The reason: most email fraudsters are after money, not corporate secrets. That makes these low-ranking industries less attractive than those frequently engaged in high-value transactions with complex and multifaceted supply-chain and customer relationships that may be more easily exploited for financial gain.
But no industry was immune to email fraud. Even the lowest-ranked industries experienced dozens of email fraud attacks per organisation in 2017. Overall, roughly 80% of businesses experienced an email fraud attack.
Get Healthy, Stay Healthy: A healthier online business starts today and it begins with you!
We're passionate about helping you grow and make your impact
Continue being informed
Monthly vulnerability reports about WordPress and WooCommerce, plugins, themes.
Weekly inspiration, news and occasional with hand-picked deals. Unsubscribe anytime.