2 SQL Injections - WordPress Security DEC, 2020
Be informed about the latest SQL Injections, identified and reported publicly in December 2020. As these WordPress Security vulnerabilities have a severe negative impact for any website, consider a security AUDIT. The following PLUGINS made headlines just last month.
- User Registration & User Profile – Profile Builder < 3.3.3 - Authenticated Blind SQL Injection
- Profile Builder is the all in one user profile plugin for WordPress. Easy to use user profile plugin for creating front-end login, user registration and edit profile forms by using shortcodes. Restrict Content based on user role or logged in status. Manage user roles and capabilities using the built in Role Editor. Active installations: 50,000+
- DiveBook <= 1.1.4 - Unauthenticated SQL Injection
- This plugin has been closed as of December 9, 2020 and is not available for download. This closure is temporary, pending a full review.
Protect your WordPress: BEFORE IT'S TOO LATE! You will also protect your customers, your reputation and your online business!
BRIEF: SQL injection is a code injection technique, used to attack data-driven applications, in which malicious SQL statements are inserted into an entry field for execution.
What is SQL Injection?
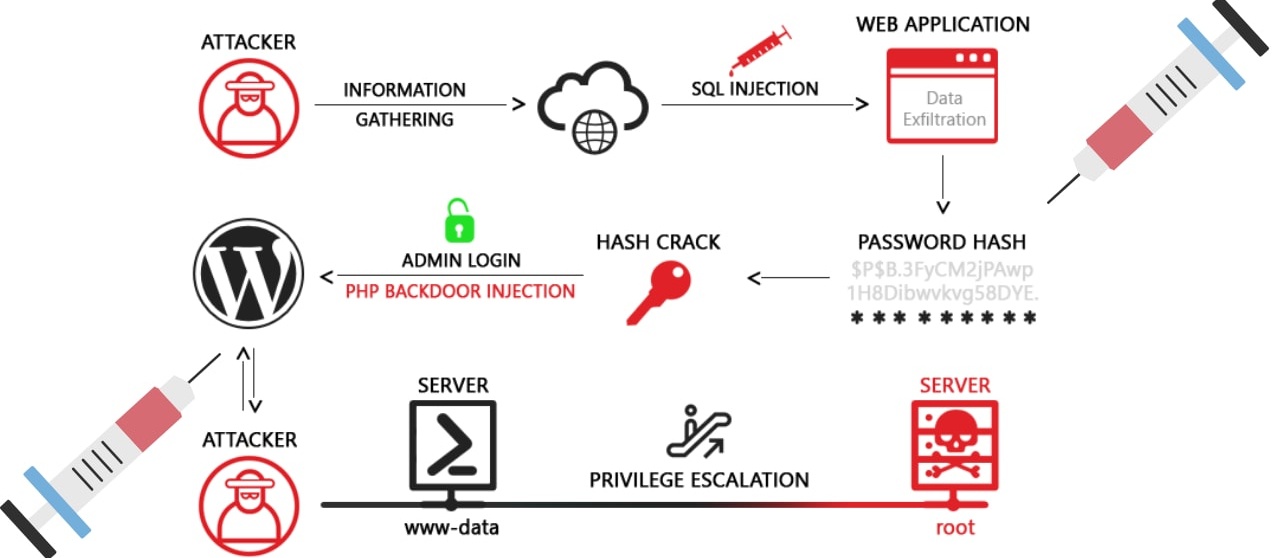
SQL injection is a web security vulnerability that allows an attacker to interfere with the queries that an application makes to its database. It generally allows an attacker to view data that they are not normally able to retrieve. This might include data belonging to other users, or any other data that the application itself is able to access.
In many cases, an attacker can modify or delete this data, causing persistent changes to the application's content or behaviour. In some situations, an attacker can escalate an SQL injection attack to compromise the underlying server or other back-end infrastructure, or perform a denial-of-service attack.
What is the impact of an SQL Injection?
A successful SQL injection attack can result in unauthorised access to sensitive data, such as passwords, credit card details, or personal user information. Many high-profile data breaches in recent years have been the result of SQL injection attacks, leading to reputational damage and regulatory fines. In some cases, an attacker can obtain a persistent backdoor into an organization's systems, leading to a long-term compromise that can go unnoticed for an extended period.
What kind of SQL Injections are exploited?
There are a wide variety of SQL injection vulnerabilities, attacks, and techniques, which arise in different situations. Some common SQL injection examples include:
- Retrieving hidden data, where you can modify an SQL query to return additional results.
- Subverting application logic, where you can change a query to interfere with the application's logic.
- UNION attacks, where you can retrieve data from different database tables.
- Examining the database, where you can extract information about the version and structure of the database.
- Blind SQL injection, where the results of a query you control are not returned in the application's responses.
Get Healthy, Stay Healthy: A healthier online business starts today and it begins with you!
Do you suspect any SQL Injections within your WordPress? Contact us today for a free scan!
We’re passionate about helping you grow and make your impact
Continue being informed
Monthly vulnerability reports about WordPress and WooCommerce, plugins, themes.
Weekly inspiration, news and occasional with hand-picked deals. Unsubscribe anytime.