SSRF OCT 2023
Server-Side Request Forgery OCT 2023
Managed Woo/WP Security Report
Be informed about the latest Server-Side Request Forgery OCT 2023, identified and reported publicly. As these SSRF OCT 2023 vulnerabilities have a severe negative impact on any WordPress Security, consider our security audit.
It is a -33% DECREASE compared to previous month, as specifically targeted Server-Side Request Forgeries. Consider for your online safety, a managed WP/Woo Security AUDIT, - OR - switching with a TOP10LIST alternative WP Security Plugin – OR – Hire us for your recurrent needs of managed WordPress Security and managed WooCommerce Security.
The following cases made headlines PUBLICLY in the SSRF OCT 2023 & Server-Side Request Forgery OCT 2023 category:
WHO needs managed WP security? EVERYBODY!
Today's reality needs a Web Application Firewall (WAF) plus an Intrusion Prevention System (IPS) to mitigate "gazillion" different threats in your WordPress. Get your Server-Side Request Forgery OCT 2023 Patch Management.
| SSRF & Server-Side Request Forgery reported in 2023 so far | 36 |
WHO needs managed WP Maintenance? EVERYBODY!
Today’s reality requires daily clean-ups with database optimisations, weekly updates and upgrades for both free & premium modules, plus the occasional emergency changes when critical vulnerabilities are publicly disclosed without patches. Order Server-Side Request Forgery OCT 2023 Patch Management.
BRIEF: Server-Side Request Forgery OCT 2023 is a type of hosting server security exploit, where an attacker abuses the basic functionality of a hosting environment, causing it to access or manipulate information in the realm of that server that would otherwise not be directly accessible to the attacker.
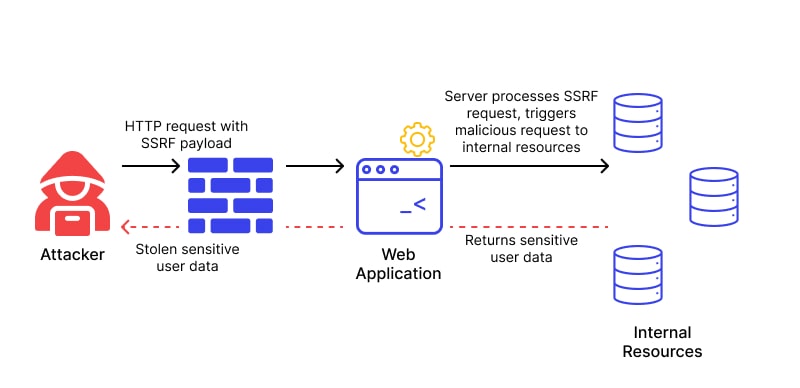
What is Server-Side Request Forgery OCT 2023?
Server-Side request forgery (also known as SSRF) occur whenever a WordPress or WooCommerce is fetching a remote resource without validating the user-supplied URL. It allows an attacker to coerce the public side (front-end) to send a crafted request to an unexpected destination (back-end, database, files), even when protected by a firewall, or another type of network access control list (ACL).
As modern websites provide end-users with convenient features, fetching an URL becomes a common tactic. As a result, the incidence of SSRF 2023 is increasing. Also, the severity of SSRF 2023 is growing higher due to publicly accessible cloud services and the complexity of their architectures.
What is the impact of a SSRF OCT 2023 attack?
A successful SSRF 2023 attack can often result in unauthorised actions on the hosting environment or access to data within WordPress and WooCommerce, or on other back-end systems that the application can communicate with like database or 3rd party integrations (payment modules, seo modules, marketing modules, analytics modules, etc). In some situations, the SSRF vulnerability might allow an attacker to perform arbitrary command execution, compromising everything.
A specific and successful SSRF 2023 exploit that causes connections to external systems, always generates malicious direct attacks, that appear to originate from the domain itself or hosting environment, continuing its attack towards the next vulnerable external system.
Security is not a single-task job
Need managed WP Security and got no clue where to start? Hire an expert. Pay a coffee per week, its cheaper than 1 hour for a freelancer.
Not sure that our recurrent security offer is worthy of long-term consideration? Contact us today for a Server-Side Request Forgery audit! Decide after you compare RISK + IMPACT versus COST.
We’re passionate about helping you grow and make your impact
Continue being informed
Monthly vulnerability reports about WordPress and WooCommerce, plugins, themes.
Weekly inspiration, news and occasional with hand-picked deals. Unsubscribe anytime.