Cybercrime PAY$$ phishing scams insider to deploy Ransomware
A new phishing scams approach has been observed trying to recruit staff members by providing them to pay $1 million in bitcoins to deploy Black Kingdom ransomware on a business’ server and network as part of an insider threat scheme. Using a simple tactic, called “Nigerian Ransomware”.

What is Nigerian Ransomware?
Directly explained by Nigeria (https://scamwatch.ng/content/what-ransomware): "Ransomware is malicious software with one aim in mind: to extort money from its victims. It's one of the most prolific criminal business models in existence today, mostly thanks to the multimillion-dollar ransoms criminals demand from individuals and corporations. These demands are very simple: pay the ransom, or have your operations severely compromised or shut down completely."
So, why is then named Nigerian? Because it asks you to deploy it. Long since jokes sparked this low-technical security menace. Today is not that funny anymore. While the most common cyber-attack we see from Nigerian actors (and most damaging attack globally) is business email compromise (BEC), it makes sense that a Nigerian actor would fall back on using similar social engineering techniques, even when attempting to successfully deploy a more technically sophisticated attack like ransomware.
Protect your WordPress from public phishing scams BEFORE IT’S TOO LATE! You will also protect your customers, your reputation and your online business!
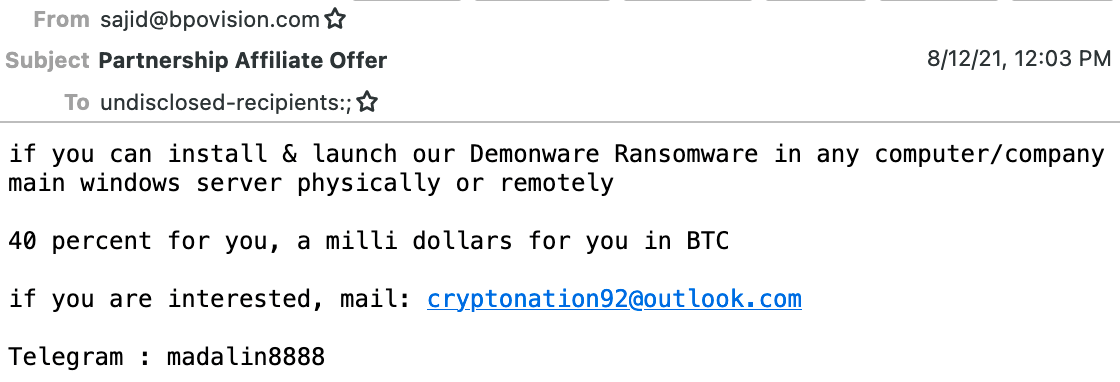
How Nigerian phishing scams Ransomware work?
The sender (Nigerian hacker IMPERSONATOR) tells the employee of the targeted company, that if they can deploy ransomware on a business computer or server, then they would be paid $1 million in bitcoin or 40% of the assumed $2.5 million ransom. The employee is told they can launch the ransomware physically (via USB) or remotely (via browser download). The sender provided 2 approaches to call them if the employee is interested-- an Outlook e-mail account and a Telegram username."
Historically, ransomware has been delivered via e-mail attachments or, more just recently, utilizing direct network gain access to obtained through things like unsecured VPN accounts or software application vulnerabilities. Seeing a star effort to utilize fundamental social engineering strategies to convince an internal target to be complicit in an attack versus their company was noteworthy.
How do they target specific company employees?
The method is using LinkedIn to gather business email addresses of senior-level executives, once again highlighting how business email compromise (BEC) attacks originating from Nigeria continue to develop and expose companies to sophisticated attacks like ransomware. Something cheap and fast. The method explained by Tim Erlin, vice president of product management and strategy at Tripwire:
"There's always been a blurry line between cyberattacks and social engineering, and this is an example of how the two are intertwined. As people become better at recognizing and avoiding phishing scams, it should be no surprise to see attackers adopt new tactics to accomplish their goals. The idea of a disgruntled insider as a cybersecurity threat isn't new. As long as organizations require employees, there will always be some insider risk. The promise of getting a share of the ransom might seem attractive, but there are almost zero guarantees that this kind of complicity will be rewarded, and someone taking this attacker up on their offer would likely get caught".
Nigerian Ransomware: An Inside Look
In this case, it is easy to become a Nigerian hacker. You are simply required to download the ransomware from GitHub and socially engineer someone to release the malware for them. This shows the appeal of ransomware-as-a-service, as it reduces the barrier of entry for less technically sophisticated actors to enter the ransomware area. The next step is to identify a few LinkedIn Connections by Finding Targets Through Social Networks.
Threat analysis like this assists us better comprehend the bigger picture with additional context-- something we're not able to do by only taking a look at conventional signs of compromise and raw data. Utilizing these special intelligence collection techniques, we can acquire a deeper level of insight to assist much better comprehend emerging cyber hazards, and to much better protect our consumers.
Weird reality
Can you trust your staff members? Your remote employees? Your external providers? Your vendors? And most especially for ex-employees, ex-service providers, ex-vendors. How tempting is the potential 40% off the shared revenue extorted to them?
Get Healthy, Stay Healthy! A healthier online business starts today and it begins with you. Let’s identify and block all your phishing scams.
We’re passionate about helping you grow and make your impact
Continue being informed
Monthly vulnerability reports about WordPress and WooCommerce, plugins, themes.
Weekly inspiration, news and occasional with hand-picked deals. Unsubscribe anytime.







