
State-sponsored attackers and established cybercriminals usually reserve their efforts for the biggest, most high-profile targets. But in 2017, they began going after smaller targets. Advanced persistent threats (APTs) are far more difficult to detect and defend against than other types of cyber attacks. They have significant resources, proven capabilities and sophisticated tools. They can more easily target the human factor and warrant close scrutiny.
The Lazarus Group
From Wikipedia, the free encyclopedia: Lazarus Group (also known as HIDDEN COBRA, BlueNoroff) is a cybercrime group made up of an unknown number of individuals. While not much is known about the Lazarus Group, researchers have attributed many cyber attacks to them over the last decade.
History:
The earliest known attack that the group is responsible for is known as "Operation Troy", which took place from 2009–2012. This was a cyber-espionage campaign that utilized an unsophisticated distributed denial-of-service attack (DDoS) techniques to target the South Korean government in Seoul. They are also responsible for attacks in 2011 and 2013. It is possible that they were also behind a 2007 attack targeting South Korea, but that is still uncertain.
Our only security is our ability to change. ~ John Lilly
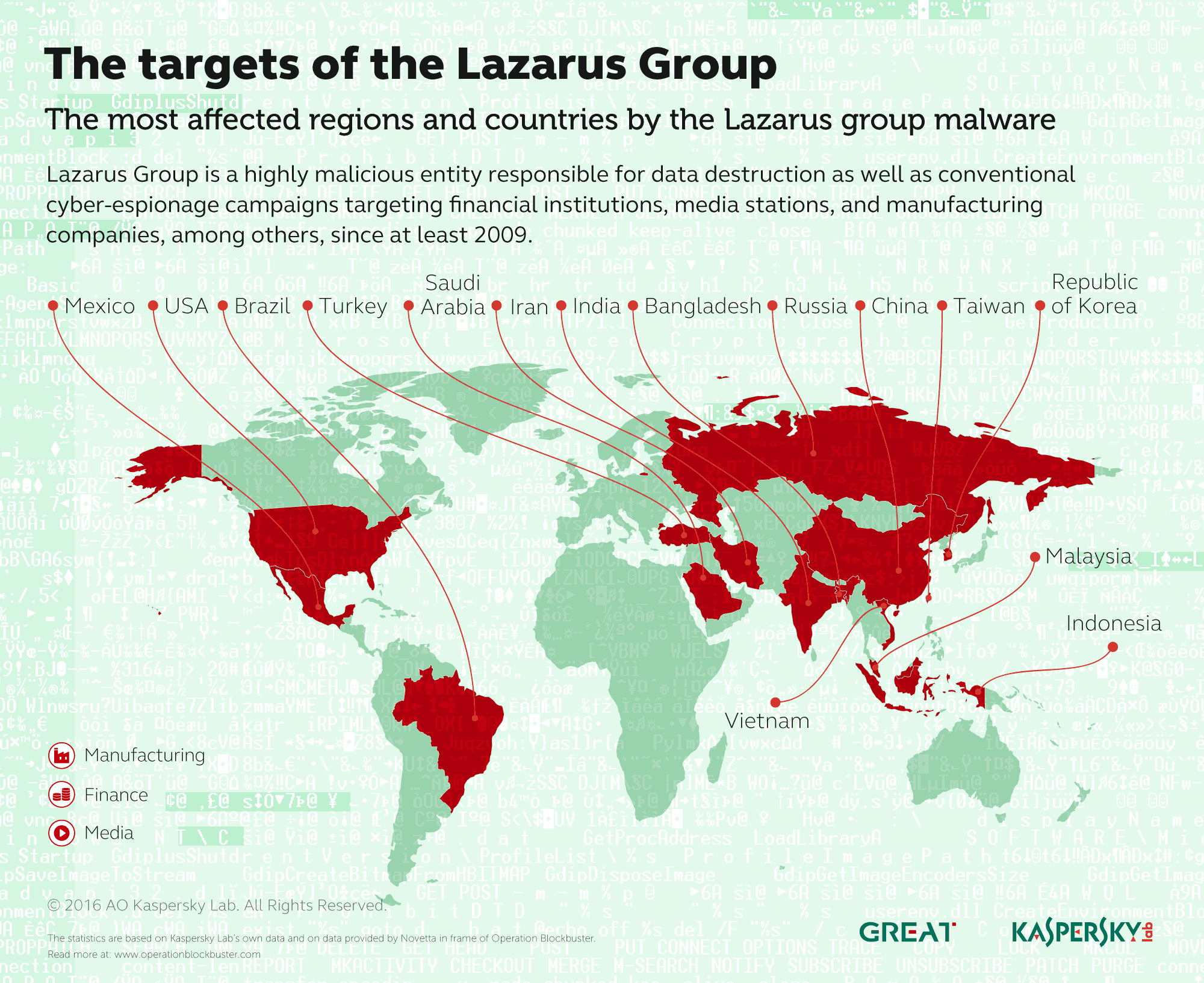
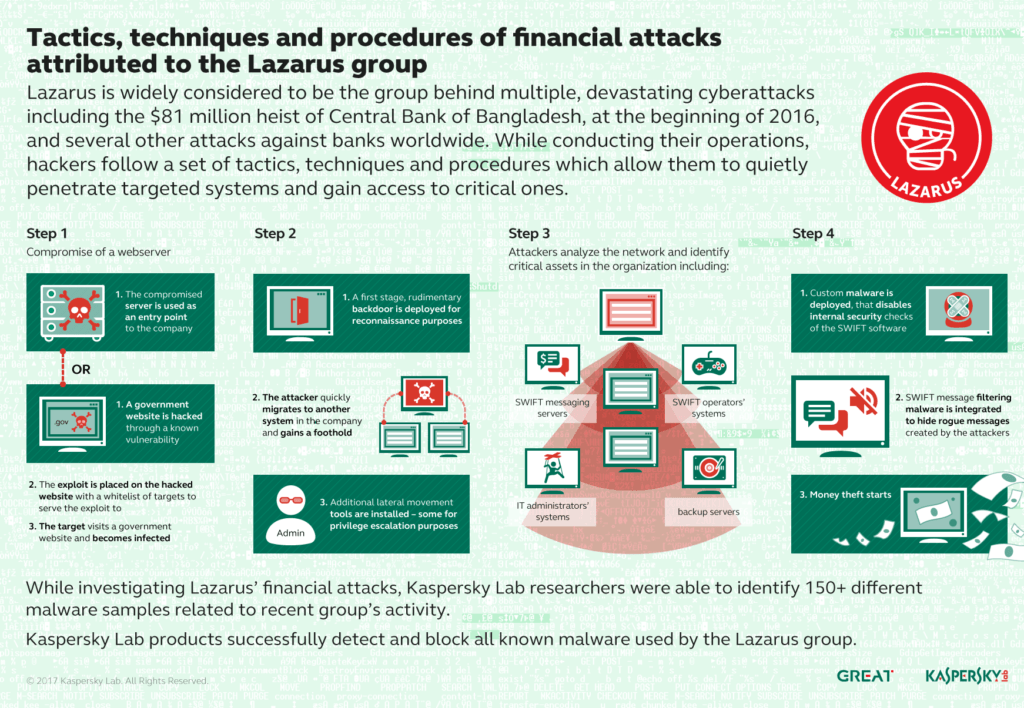
A notable attack that the group is known for is the 2014 attack on Sony Pictures. The Sony attack used more sophisticated techniques and highlighted how advanced the group has become over time. The Lazarus Group were reported to have stolen $12 million from the Banco del Austro in Ecuador and US$1 million from Vietnam's Tien Phong Bank in 2015. They have also targeted banks in Poland and Mexico. The 2016 bank heist included an attack on the Bangladesh Bank, successfully stealing US$81 million and was attributed to the group. In 2017 the Lazarus group was reported to have stolen US$60 million from the Far East International Bank of Taiwan although the actual amount stolen was unclear and most of the funds were recovered.
At the end of the day, the goals are simple: safety and security. ~ Jodi Rell
Protect your WordPress: BEFORE IT'S TOO LATE! You will also protect your customers, your reputation and your online business!
APT: Lazarus Group
The Lazarus Group is widely recognised as a threat actor affiliated with North Korea. It has launched both financially motivated and espionage activities against banks, governments and many other agencies before. But in 2017, it initiated multistage attacks against individual people to steal cryptocurrency and against point-of-sale (POS) infrastructure to steal consumer credit card data. To our knowledge, this was the first documented case of a state-sponsored attack against POS systems for financial gain.
Interestingly, the Lazarus Group planted Russian words within their code, to derail investigators and avoid attribution. The code contained grammar errors a native Russian speaker wouldn’t make, and sentences were likely translated using online tools.
Lazarus Group is one of the most active groups in terms of attacks against financial institutions and is trying to actively infect different victims in several regions. Their operations are still ongoing, and in fact, their most recent malware samples were found in March 2017. At the moment we believe BlueNoroff is probably the most serious threat against banks.
Get Healthy, Stay Healthy: A healthier online business starts today and it begins with you!
We're passionate about helping you grow and make your impact
Continue being informed
Monthly vulnerability reports about WordPress and WooCommerce, plugins, themes.
Weekly inspiration, news and occasional with hand-picked deals. Unsubscribe anytime.

