
Back in 2013, a web publishing company, Interconnect/IT, released a handy tool for finding and replacing text in a website’s database. This tool, a stand-alone file published as “searchreplacedb2.php”, includes built-in WordPress compatibility that makes working with WordPress databases a breeze.
Unfortunately, since the first public version, it did not include any authentication or security measures, which makes infecting WordPress databases equally easy. But the present version, 3.1.0, is essentially the same tool and still does not include any security measures (besides a warning). So updating to the latest version doesn’t make it any safer.
During the last few weeks, the Security Services Team from Wordfence has noticed a spike in infections using this script. The hackers use their botnets to look for the script all over a target site. The popularity of this script makes several well-known themes and plugins to use this script. Thus, when you use those themes and plugins, you’re a vulnerable WordPress owner.
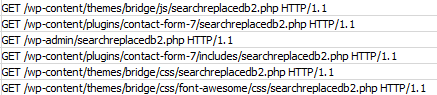
What to Do If You Have Been Hacked?
If you have searchreplacedb2.php unsecured on your WordPress site, then the odds are high that you have probably been hacked. If you have it and your users are being redirected away, then you have definitely been hacked. Head to our order page and let the owl power WordPress Security experts handle it for you.
Protect your WordPress: BEFORE IT’S TOO LATE! You will also protect your customers, your reputation and your online business!
Not sure if you have this issue? Can you afford to pretend that all is ok?
Head to our security audit page and let us search after this extremely dangerous vulnerability right now!

![7 SIGNS YOUR WORDPRESS SECURITY IS HACKED [INFOGRAPHIC] 2 HACKING](https://owlpower.eu/wp-content/uploads/2019/03/hacking-256x256.png)







