
ALERT: 14 XSS JAN 2021 - Cross-Site Scripting JAN 2021 Blast
WordPress Security Report
Be informed about the latest Cross-Site Scripting, identified and reported publicly in January 2022. As these XSS JAN 2021 vulnerabilities have a severe negative impact on any WordPress Security, consider our FREE security AUDIT.
An estimated 1.692.000 active WordPress installations are susceptible to this attack type, considering only the publicly available numbers. The estimated number can increase by 20-25% with premium versions as they are private purchases.
Furthermore, the initial estimation can triple if we consider the already patched versions BUT NOT UPDATED by owners, as the vulnerability remains active within their domain. As these owners start changing their hosting provider (due to constant unexplained issues), they actively migrate these vulnerabilities behind protected areas, possibly exposing other clean WP to different attack types.
It is a 27% increase compared to December 2020. Read more about our previous report here: 11 XSS – Cross-Site Scripting – WordPress Security DEC. The following cases made headlines PUBLICLY just last month in the XSS JAN 2021 category:
- Modern Events Calendar Lite < 5.16.5 - Authenticated Stored Cross-Site Scripting (XSS)
- WordPress event calendar plugin is the best tool used for managing events websites. Modern Events Calendar is a comprehensive events management plugin Modern Events Calendar is a responsive, mobile-friendly, FREE, and comprehensive events management plugin which is extremely user-friendly and well-designed for displaying the events calendar on the websites, ever easier. Active installations: 70,000+
- Under Construction < 3.86 - Authenticated Stored Cross-Site Scripting (XSS)
- Create an Under Construction Page, Maintenance Mode Page, Coming Soon Page or a Landing Page that takes less than a minute to install & configure. Under Construction won’t waste your time! It’s simple, fast, efficient & user-friendly with great templates users love. Active installations: 500,000+
- Stockdio Historical Chart < 2.8.1 - Reflected Cross-Site Scripting (XSS)
- Stockdio Historical Chart contains a plugin and a widget that provide the means to display a live chart with intraday and historical prices and information for stock, index, currencies or commodities. Over 65 different stock exchanges and a large number of market indices, currencies and commodities are supported. Active installations: 1,000+
- WP Shieldon – WordPress Firewall 1.6.3 - Unauthenticated Cross-Site Scripting (XSS)
-
WARNING: Plugin closed: no known fix.
-
- FV Flowplayer Video Player < 7.4.38.727 - Authenticated Stored Cross-Site Scripting (XSS)
- Custom HTML 5 video on your own site with Flash fallback for legacy browsers is here. FV Player is a free, easy-to-use, and complete solution for embedding FLV or MP4 videos into your posts or pages. With MP4 videos, FV Player offers 98% coverage even on mobile devices. Active installations: 40,000+
- Easy Contact Form Pro < 1.1.1.9 - Authenticated Stored Cross-Site Scripting (XSS)
-
WARNING: Plugin closed: no known fix.
-
- WP Quick FrontEnd Editor <= 5.5 - Authenticated Settings Change leading to Stored XSS
-
WARNING: Plugin closed: no known fix.
-
Protect your WordPress: BEFORE IT'S TOO LATE! You will also protect your customers, your reputation and your online business!
- Custom Global Variables <= 1.0.5 - Stored Cross-Site Scripting (XSS)
-
WARNING: Plugin closed: no known fix.
-
- Modal Survey < 2.0.1.8.2 - Authenticated Reflected Cross-Site Scripting (XSS)
- Modal Survey is a Premium WordPress Plugin to get your visitors voice through an attention-grabber poll. Provides a lot of customization options including unlimited surveys, questions and answers with animated display. It has an ability to offer a link at the end of survey, thus much more users will fill out the poll. Active installations: Not public info
- WP24 Domain Check < 1.6.3 - Authenticated Stored Cross-Site Scripting (XSS)
- WP24 Domain Check allows users to check domains if they are free for registration. The responsive form could be easily intregrated via shortcode or widget. Labels and colors are customizeable through the settings page. Active installations: 1,000+
- Stripe Payments < 2.0.40 - Authenticated Stored Cross-Site Scripting (XSS)
- The Stripe Payments plugin allows you to accept credit card payments via Stripe payment gateway on your WordPress site easily. It has a simple shortcode that lets you put Stripe “Buy Now” buttons anywhere on your site for a product or service. You can accept donation via Stripe also. Active installations: 40,000+
- WP Paginate < 2.1.4 - Authenticated Stored Cross-Site Scripting (XSS)
- WP-Paginate is a simple and flexible pagination plugin which provides users with better navigation on your WordPress site. In addition to increasing the user experience for your visitors, it has also been widely reported that pagination increases the SEO of your site by providing more links to your content. Active installations: 40,000+
- Orbit Fox by ThemeIsle < 2.10.3 - Authenticated Stored Cross Site Scripting
- Extend your theme functionality with Orbit Fox with various modules like Social Media Share Buttons & Icons, Uptime Monitoring, Google Analytics, custom menu-icons, one click import page templates, page builder addons and free stock featured images. Active installations: 400,000+
- Advanced Custom Fields < 5.8.12 - Cross-Site Scripting in Select2 dropdowns
- Use the Advanced Custom Fields plugin to take full control of your WordPress edit screens & custom field data. Add fields on demand. Our field builder allows you to quickly and easily add fields to WP edit screens with only the click of a few buttons! Add them anywhere. Fields can be added all over WP including posts, users, taxonomy terms, media, comments and even custom options pages! Active installations: 1+ million
Get Healthy, Stay Healthy: A healthier online business starts today and it begins with you!
BRIEF: Cross-Site Scripting JAN 2021 is a type of security vulnerability typically found in web applications. XSS attacks enable attackers to inject client-side scripts into web pages viewed by other users. A cross-site scripting vulnerability may be used by attackers to bypass access controls such as the same-origin policy.
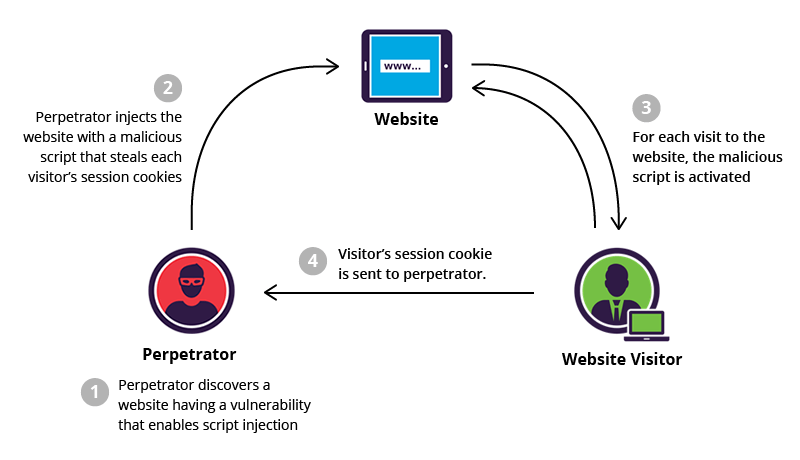
What is Cross-Site Scripting JAN 2021?
Cross-Site Scripting (XSS) attacks are a type of injection, in which malicious scripts are injected into otherwise benign and trusted websites. XSS attacks occur when an attacker uses a web application to send malicious code, generally in the form of a browser side script, to a different end user. Flaws that allow these attacks to succeed are quite widespread and occur anywhere a web application uses input from a user within the output it generates without validating or encoding it.
An attacker can use XSS to send a malicious script to an unsuspecting user. The end user’s browser has no way to know that the script should not be trusted, and will execute the script. Because it thinks the script came from a trusted source, the malicious script can access any cookies, session tokens, or other sensitive information retained by the browser and used with that site. These scripts can even rewrite the content of the HTML page.
What is the impact of a XSS JAN 2021 attack?
The actual impact of an XSS attack generally depends on the nature of the application, its functionality and data, and the status of the compromised user. For example:
- In a simple public application, where all users are anonymous and all information is public, the impact will often be minimal. Nothing else to steal.
- In an application holding sensitive or private/personal data, such as banking transactions, emails, or healthcare records, the impact will usually be serious.
- If the compromised user has elevated privileges within the application, then the impact will generally be critical, allowing the attacker to take full control of the vulnerable application and compromise all users, owners and their data.
What kind of XSS attacks are exploited?
- Reflected XSS, where the malicious script comes from the current HTTP request.
- Stored XSS, where the malicious script comes from the website's database.
- DOM-based XSS, where the vulnerability exists in client-side code rather than server-side code.
Get Healthy, Stay Healthy: A healthier online business starts today and it begins with you!
Do you suspect any Cross-Site Scripting within your WordPress? Contact us today for a free scan!
We’re passionate about helping you grow and make your impact
Continue being informed
Monthly vulnerability reports about WordPress and WooCommerce, plugins, themes.
Weekly inspiration, news and occasional with hand-picked deals. Unsubscribe anytime.


