
WP RCE MAR 2024
WP Remote Code Execution
Be informed about the latest WP Remote Code Execution, identified and reported publicly. WP RCE MAR 2024 is a +600% INCREASE compared to previous month. Consider for your online safety, a managed WP/Woo security AUDIT, – OR – switching with a TOP10LIST alternative WP Security Plugin – OR – Hire us for your recurrent needs of managed WP Security.
What is RCE?
TLDR: RCE vulnerabilities are used to deploy and execute ransomware on a vulnerable domains. While these are some of the most common impacts of RCE vulnerabilities, an RCE vulnerability can provide an attacker with full access and control over the targeted site.
RCE is short for Remote Code Execution. A security flaw in software or hardware allowing arbitrary code execution. A program that is designed to exploit such a vulnerability is called an arbitrary code execution exploit. The ability to trigger arbitrary code execution over a network (especially via a wide-area network such as the Internet) is often referred to as remote code execution (RCE). Read more on wikipedia.org: Arbitrary code execution.
Need managed WP security?
Today's reality needs a Web Application Firewall (WAF) plus an Intrusion Prevention System (IPS) to mitigate specific threats in your WordPress. Get your WP RCE MAR 2024 Patch Management.
The following cases made headlines PUBLICLY just last month in the WP RCE MAR 2024 category:
| WP Remote Code Execution (RCE) reported in 2023: | 38 |
| WP Remote Code Execution (RCE) reported in 2024: | 6 |
Need managed WP Maintenance?
Today's reality requires daily clean-ups with database optimisations, weekly updates and upgrades for both free & premium modules, plus the occasional emergency changes when critical vulnerabilities are publicly disclosed without patches. Order your WP RCE MAR 2024 Patch Management.
BRIEF: The umbrella of remote code execution is incredibly broad, and it includes a huge variety of attacks and malicious code. Most commonly, attackers exploit zero-day vulnerabilities to gain deeper access.
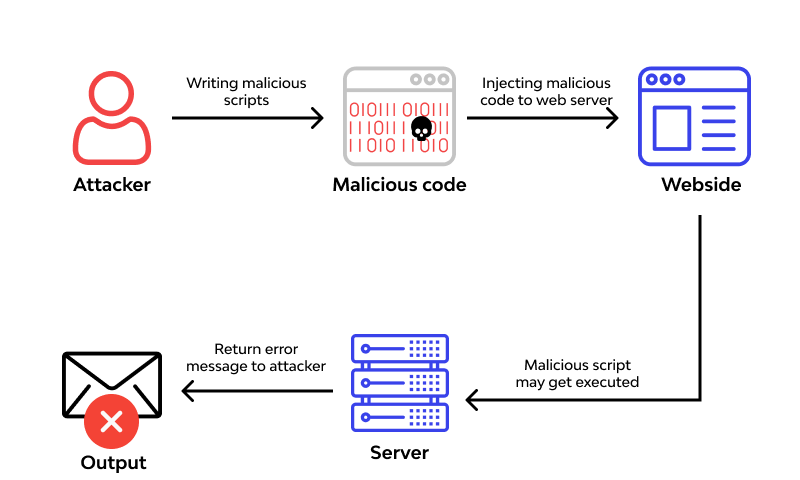
What is Remote Code Execution?
Remote code execution (RCE) refers to a class of cyberattacks in which attackers remotely execute commands to place malware or other malicious or backdoor code. In an RCE attack, there is no need for user input from privileged accounts like admin, shop manager, editor, etc. A remote code execution vulnerability always compromises sensitive and private data.
RCE: How it Works
- Attacker identifies a specific vulnerability
- In exploiting that vulnerability, they remotely insert malicious code
- Once the hackers has access, they compromise private data or use your domain for nefarious purposes.
What is the Goal of an RCE Attack?
Once attackers have access via remote code execution, the possibilities for what they can do are nearly limitless. RCE attacks have been used to perform everything (deleting, altering, blocking, exfiltrating, stealing, defacing, spying). This is why RCE prevention is such a high priority for cybersecurity.
What is the Impact of Remote Code Execution Vulnerability?
Neglecting RCE vulnerabilities creates with DIRECT and UNRESTRICTED access, where none should have from external reach. Because remote code execution covers such a wide range of attacks, it’s safe to say that RCE can cause nearly any level of damage. In short: exactly what the attacker wants ... and more.
Security is not a single-task job
Need managed WP Security and got no clue where to start? Hire an expert. Pay a coffee per week, its cheaper than 1 hour for a freelancer.
Not sure that our recurrent security offer is worthy of long-term consideration? Contact us today for a RCE AUDIT. Decide after you compare RISK + IMPACT versus COST.
We’re passionate about helping you grow and make your impact
Continue being informed
Monthly vulnerability reports about WordPress and WooCommerce, plugins, themes.
Weekly inspiration, news and occasional with hand-picked deals. Unsubscribe anytime.


