
Social Engineering exploits
Human interaction and commerce are increasingly digital, and threat actors are adapting to that reality. They are following shifting trends, usage patterns and popular interests to attack people through social media channels. Many of these attacks rely on social engineering. Others simply take advantage of inclinations for immediate gratification, improved status or even the reward of “getting something for nothing.” But as the old adage goes, there is no such thing as a free lunch. The hidden costs of a bargain in social media channels can often be the credential loss to phishing, coin mining through browser hijacking and malware infections.
A large social media BOTNET built by exploiting an early version of the Facebook API and a legitimate but outdated version of a third-party app. The botnet operators convinced Facebook users to install the third-party app and provide an API access token in exchange for more likes on their posts. In reality, the app supported a botnet used to generate spam on a variety of branded Facebook pages. Facebook has since made changes to prevent this type of abuse. But the scheme is a window into the myriad ways threat actors can prey on social media users.
Angler phishing, also known as social media support fraud, is another risk to social media users. In angler phishing, attackers insert themselves into conversations between people and brands they trust using lookalike social media handles to steal personal information. Financial services brands are the most likely to be abused in this way. About 55% of all angler phishing attacks targeted financial institutions and their customers.
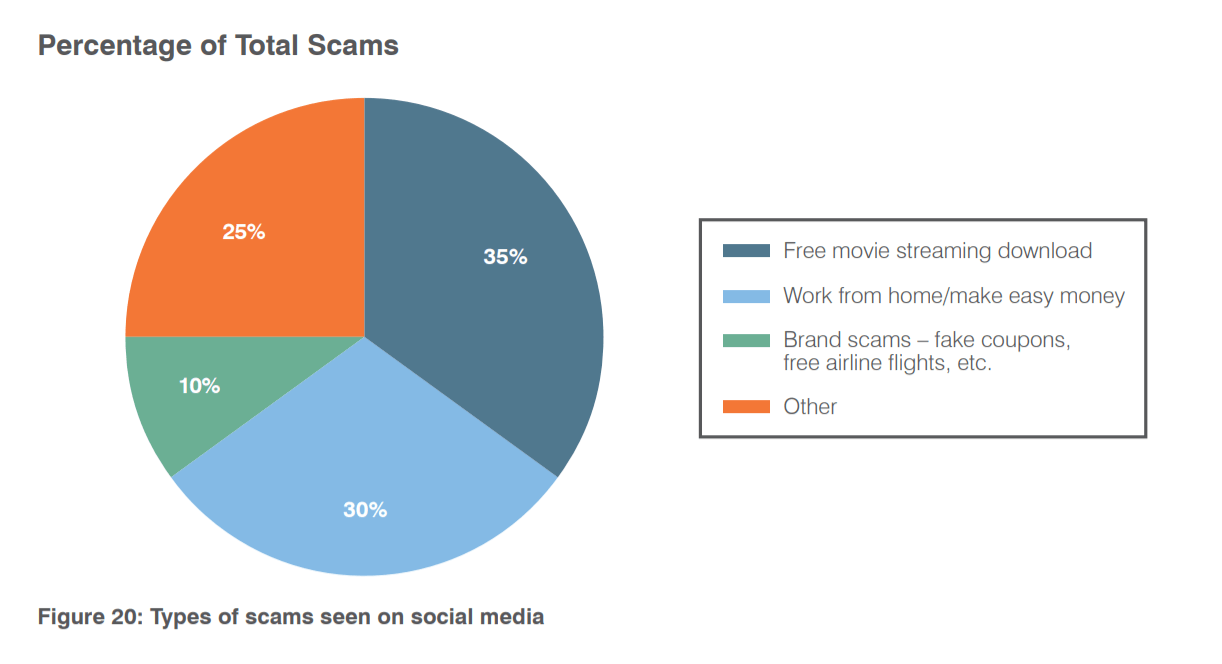
Customers of entertainment and media companies experience less than half of this. They accounted for 25% of all social media support fraud. The remaining 20% of angler phishing targets customers of technology, food and telecommunications brands. More traditional social engineering scams include posting bogus coupons and links to malicious pages claiming to be free offers, often for movies or performances. In other cases, attackers send carefully engineered phishing scams as direct messages to social media users.
Protect your WordPress: BEFORE IT'S TOO LATE! You will also protect your customers, your reputation and your online business!
The distribution of scam types we observe on social channels, either posted as links or fake social media pages:
Most recently, a large number of websites are impersonating major brands but residing on unrelated domains. Attacker and fraudsters are buying “clean,” unused and expired domains from a robust secondary market. These URLs are valid and have solid reputation scores, making detection by WordPress Security tools more difficult. Threat actors count on users simply clicking links and being fooled by the content of the sites rather than noticing the unrelated URLs. We have seen this kind of brand impersonation across industries, though it is often focused on selling luxury goods and clothing items at a too-good-to-be-true discount. Once users provide credit card information, the site operators rarely deliver what they promise. They deliver cheap counterfeit merchandise and may even resell credit card information.
Get Healthy, Stay Healthy: A healthier online business starts today and it begins with you!
We're passionate about helping you grow and make your impact
Continue being informed
Monthly vulnerability reports about WordPress and WooCommerce, plugins, themes.
Weekly inspiration, news and occasional with hand-picked deals. Unsubscribe anytime.










