It is by far the utmost annoyance online: clicking on a link, waiting for that “sought-out something” to load, just to get greeted by the information, that your journey just hit a dead-end. You face your disappointment, start from scratch, then the same thing happens again on the same site….
WP SERVICES
We created this curated post as a Hyper Guide to WordPress Monitoring. Use these techniques and gain valuable insights from your WordPress. We noticed, that resources regarding WordPress monitoring (even about general monitoring) are scarce. There a quite a few, but they recommend the same few tips over and over….
It was Peter Drucker who said, “What gets measured gets improved.” If you do a simple search after “What gets measured gets …”, you’ll notice a lot of positive, focused and goal-oriented thinking. It is because this is how things are done. You start things, then you constantly improve. So…
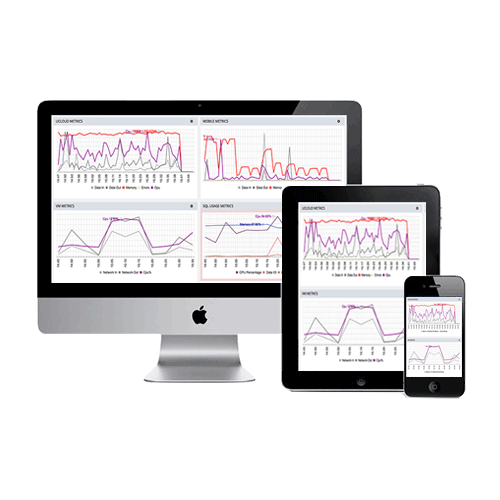
We live in a technological world so advanced for monitoring capabilities, that you can track your own car or even your child. So why not your WordPress? Well, you should track your WordPress! And the first thing you should consider is your WordPress uptime monitoring. What is WordPress uptime monitoring?…
You asked and we delivered! Greg, this one is for you! ;) One of our sweet-talking customers challenged us to overcome an issue for him and his team. We allow the account owner (mostly the business owners) to have their own account, inside our monitoring solution. Unfortunately, we’re using a…
SOCIAL PROOF features are meant to enhance the lure to accept something, as a psychology trick. When you see, that one (or more) of your friends already liked the page, you’re visiting, you are more likely to do the same thing. This is valid for purchases also, and it acts…
Social Media is present everywhere. Online and offline. Lately, I’ve seen ads with like boxes. Yeah, the most hated things join hands with social media. So, your WordPress is definitely not an exception to social media enhancements. We even bet, you have several features, provided by Social Media. However, those…
SOCIAL MEDIA COMMENTS are feature-switch options for your WordPress, meant to replace the default WP comment system with an external platform provided comments system. Mostly Facebook or Google Plus as an example; however, it exists a few more dedicated systems, like: IntenseDebate, spot.im, Disqus or Epoch from Postmatic. All these…
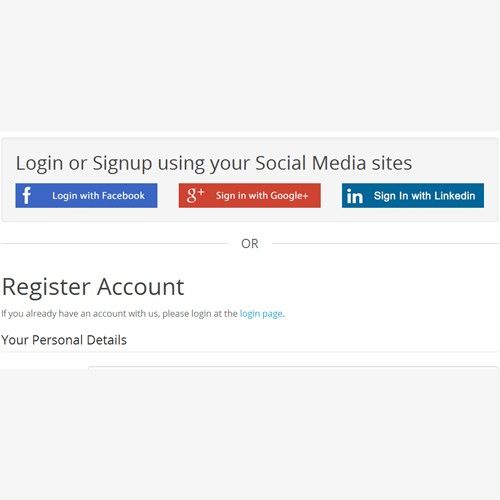
SOCIAL MEDIA LOGIN are extra features for your WordPress, an authentification process done by a social media platform to allow WP Users login associated with your WordPress. This is a hot potato subject. While its advantages to just login with a single click (even on account creation); accessing visitors own…